Cisco RV042 User Guide - Page 8
Introduction, Introduction to the Router, Introduction to VPNs, VPN Examples
 |
UPC - 745883560530
View all Cisco RV042 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 8 highlights
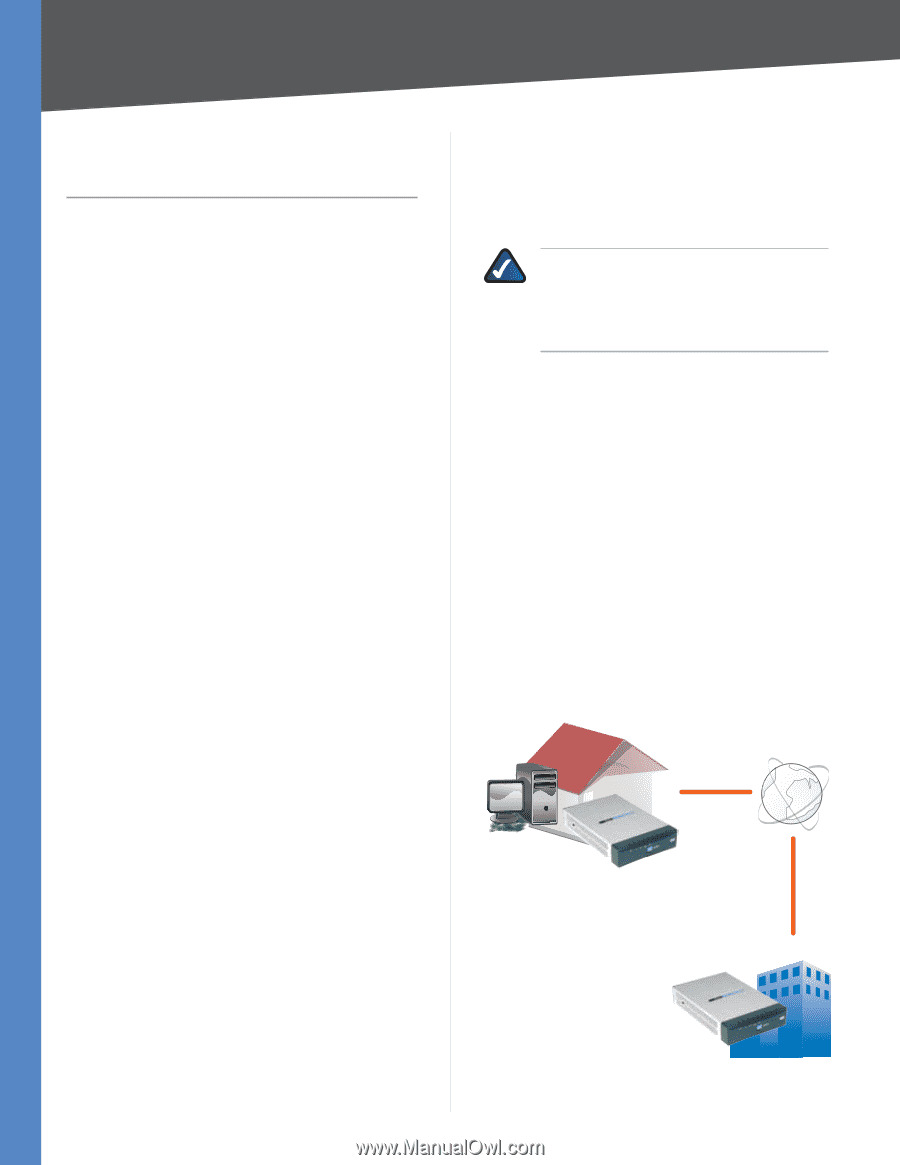
Chapter 1 Introduction Chapter 1: Introduction Introduction to the Router Thank you for choosing the Linksys 10/100 4-Port VPN Router. The Router lets multiple computers in your office share an Internet connection. The dual Internet ports let you connect a second Internet line as a backup, or you can use both Internet ports at the same time, allowing the Router to manage bandwidth demands for maximum efficiency. The Router features a built-in, 4-port, full-duplex, 10/100 Ethernet switch to connect four computers directly, or you can connect more switches to expand your network. For remote connections, up to 50 remote office or traveling users can securely connect to your office network using the Router's Virtual Private Network (VPN) capability. Use the browser-based utility to configure settings and run convenient wizards that will help you set up the Router and its access rules. Introduction to VPNs A VPN is a connection between two endpoints-a VPN Router, for instance-in different networks that allows private data to be sent securely over a shared or public network, such as the Internet. This establishes a private network that can send data securely between these two locations or networks. The private network is established by creating a "tunnel". A VPN tunnel connects the two computers or networks and allows data to be transmitted over the Internet as if it were still within those networks. A VPN tunnel uses industry‑standard encryption and authentication techniques to secure the data sent between the two networks. Virtual Private Networking was created as a cost-effective alternative to using a private, dedicated, leased line for a private network. It can be used to create secure networks linking a central office with branch offices, telecommuters, and/or professionals on the road. There are two basic ways to create a VPN connection: •• VPN Router to VPN Router •• computer (using VPN client software) to VPN Router The VPN Router creates a "tunnel" or channel between two endpoints, so that data transmissions between them are secure. A computer with VPN client software can be one of the two endpoints. 10/100 4-Port VPN Router For an IPSec VPN tunnel, the VPN Router and any computer with the built-in IPSec Security Manager (Windows 2000 and XP) can create a VPN tunnel using IPSec (Windows Vista uses a similar utility). Other Windows operating systems require additional, third-party VPN client software applications that support IPSec to be installed. NOTE: The 10/100 4-Port VPN Router supports IPSec VPN client software, including the Linksys QuickVPN software. (For more information, refer to "Appendix B: Linksys QuickVPN for Windows 2000, XP, or Vista".) For a PPTP VPN tunnel, the 10/100 4-Port VPN Router and any computer running Windows 2000 or XP can create a VPN tunnel using PPTP. VPN Examples The following are examples of a VPN tunnel between two VPN routers and a VPN tunnel between a computer using VPN client software and a VPN router. VPN Router to VPN Router For example, at home, a telecommuter uses his VPN Router for his always-on Internet connection. His Router is configured with his office's VPN settings. When he connects to his office's router, the two routers create a VPN tunnel, encrypting and decrypting data. As VPNs use the Internet, distance is not a factor. Using the VPN, the telecommuter now has a secure connection to the central office's network, as if he were physically connected. Home Internet VPN Router Central Office VPN Router VPN Router to VPN Router 1