Cisco AIR-LAP1252AG-A-K9 Software Configuration Guide - Page 134
Enabling Temporal Key Integrity Protocol (TKIP
 |
UPC - 882658140716
View all Cisco AIR-LAP1252AG-A-K9 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 134 highlights
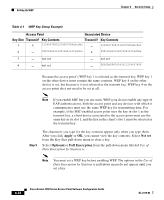
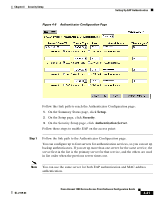
Enabling Additional WEP Security Features Chapter 4 Security Setup Follow this link path to browse to the AP Radio Advanced page: 1. On the Summary Status page, click Setup. 2. On the Setup page, click Advanced in the AP Radio row under Network Ports for the internal radio or the radio module. Follow these steps to enable MIC: Step 1 Follow the steps in the "Setting Up WEP" section on page 4-9 to set up and enable WEP. You must set up and enable WEP with full encryption before MIC becomes active. If WEP is off or if you set it to optional, MIC is not enabled. Note If you enable MIC but you use static WEP (you do not enable any type of EAP authentication), both the access point radio and any devices with which it communicates must use the same WEP key for transmitting data. For example, if the MIC-enabled access point uses the key in slot 1 as the transmit key, a client device associated to the access point must use the same key in its slot 1, and the key in the client's slot 1 must be selected as the transmit key. Step 2 Step 3 Step 4 Step 5 Browse to the AP Radio Advanced page for the internal radio or the radio module. Select MMH from the Enhanced MIC verification for WEP pull-down menu. Make sure yes is selected for the Use Aironet Extensions setting. MIC does not work if Use Aironet Extensions is set to no. Click OK. MIC is enabled, and only client devices with MIC capability can communicate with the access point. Enabling Temporal Key Integrity Protocol (TKIP) Temporal Key Integrity Protocol (TKIP), also known as WEP key hashing, defends against an attack on WEP in which the intruder uses an unencrypted segment called the initialization vector (IV) in encrypted packets to calculate the WEP key. TKIP removes the predictability that an intruder relies on to determine the WEP key by exploiting IVs. TKIP protects both unicast and broadcast WEP keys. 4-16 Cisco Aironet 1200 Series Access Point Software Configuration Guide OL-2159-03