Cisco AIR-LAP1252AG-A-K9 Software Configuration Guide - Page 152
Authenticating Client Devices Using MAC Addresses or EAP, Disallowed, Require EAP
 |
UPC - 882658140716
View all Cisco AIR-LAP1252AG-A-K9 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 152 highlights
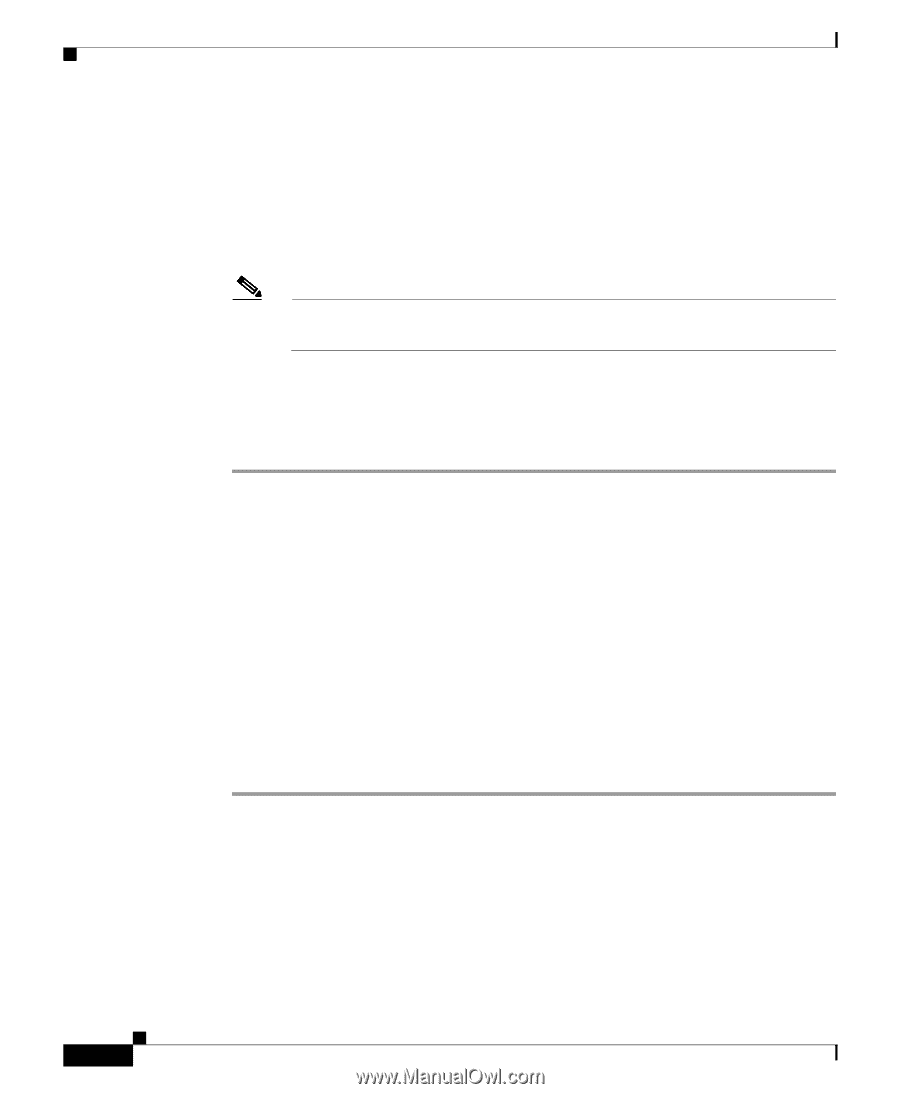
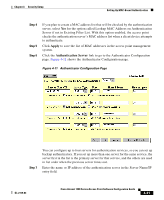
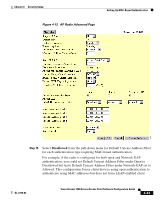
Setting Up MAC-Based Authentication Chapter 4 Security Setup devices to authenticate using MAC addresses. To force all client devices to authenticate using MAC addresses, select Disallowed for all the enabled authentication types. When you set Default Unicast Address Filter to disallowed, the radio discards all unicast traffic except packets sent to the MAC addresses listed as allowed on the authentication server or on the access point's Address Filters page. Note Client devices associated to the radio are not immediately affected when you set the Default Unicast Address Filter to disallowed. Step 16 Click OK. You return automatically to the Setup page. Client devices that associate with the access point through this radio will not be allowed to authenticate unless their MAC addresses are included in the list of allowed addresses. Authenticating Client Devices Using MAC Addresses or EAP You can set up one or both access point radios to authenticate client devices using a combination of MAC-based and EAP authentication. When you enable this feature, client devices that associate to the access point using open authentication first attempt MAC authentication. If MAC authentication succeeds, the client device joins the network; if the client is also using EAP authentication, it attempts to authenticate using EAP. If MAC authentication fails, the access point waits for the client device to attempt EAP authentication. Follow these steps to combine MAC-based and EAP authentication for client devices using IEEE 802.11 open authentication: Step 1 Step 2 Follow the steps in the "Setting Up EAP Authentication" section on page 4-20 to set up EAP. You must select Require EAP under Open authentication on the radio's AP Radio Data Encryption page to force client devices to perform EAP athentication if they fail MAC authentication. If you do not select Require EAP, client devices that fail MAC authentication might be able to join the network without performing EAP authentication. Follow the steps in the "Setting Up MAC-Based Authentication" section on page 4-29 to set up MAC-based authentication. 4-34 Cisco Aironet 1200 Series Access Point Software Configuration Guide OL-2159-03