Dell PowerConnect W-IAP92 Dell Instant 6.1.3.4-3.1.0.0 User Guide - Page 110
External RADIUS Server, Authentication Terminated on IAP, Configuring an External RADIUS Server
 |
View all Dell PowerConnect W-IAP92 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 110 highlights
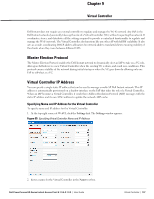
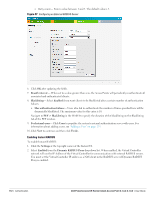
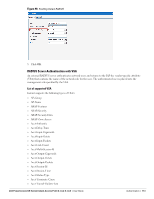
Controller (the client certificate must be signed by a known CA) before the user name is checked on the authentication server. EAP-TTLS (MSCHAPv2)- The Extensible Authentication Protocol-Tunneled Transport Layer Security (EAP-TTLS) method uses server-side certificates to set up authentication between clients and servers. However, the actual authentication is performed using passwords. EAP-PEAP (MSCHAPv2)- Protected Extensible Authentication Protocol (PEAP) is an 802.1X authentication method that uses server-side public key certificates to authenticate clients with server. The PEAP authentication creates an encrypted SSL / TLS tunnel between the client and the authentication server. Exchange of information is encrypted and stored in the tunnel ensuring the user credentials are kept secure. LEAP- Lightweight Extensible Authentication Protocol (LEAP) uses dynamic WEP keys for authentication between the client and authentication server. NOTE: Dell does not recommend to use the LEAP authentication method because it does not provide any resistance to network attacks. External RADIUS Server In the external RADIUS server, the IP address of the Virtual Controller is configured as the NAS IP address. Instant RADIUS is implemented on the Virtual Controller, and this feature eliminates the need to configure multiple NAS clients for every IAP on the RADIUS server for client authentication. Instant RADIUS dynamically forwards all the authentication requests from a NAS to a remote RADIUS server. The RADIUS server responds to the authentication request with an Access-Accept or Access-Reject message, and users are allowed or denied access to the network depending on the response from the RADIUS server. When you enable the external RADIUS server option for the network, the authenticator on the IAP sends a RADIUS packet to the local IP address. The external RADIUS server then listens and responds to the RADIUS packet. The following authentication methods are supported in Dell Instant network: Authentication Terminated on IAP Dell Instant allows EAP termination for PEAP-GTC and PEAP-MSCHAV2. PEAP-GTC termination allows authorization against an LDAP server and external RADIUS server while PEAP-MSCHAV2 allows authorization against an external RADIUS server. This will allow users to run PEAP-GTC termination with their own username and password to a local Microsoft Active Directory server with LDAP authentication. The following EAP-Type methods are described below: EAP-Generic Token Card (GTC)- This EAP method permits the transfer of unencrypted usernames and passwords from client to server. The main uses for EAP-GTC are one-time token cards such as SecureID and the use of LDAP or RADIUS as the user authentication server. You can also enable caching of user credentials on the IAP as a backup to an external authentication server. EAP-Microsoft Challenge Authentication Protocol version 2 (MS-CHAPv2)- This EAP method is widely supported by Microsoft clients.A RADIUS server must be used as the backend authentication server. If you are using the IAP's internal database for user authentication, you need to add the names and passwords of the users to be authenticated. If you are using an LDAP server for user authentication, you need to configure the LDAP server on the Virtual Controller, and configure user IDs and passwords. If you are using a RADIUS server for user authentication, you need to configure the RADIUS server on the Virtual Controller. Configuring an External RADIUS Server To configure an external RADIUS server for a wireless network: 1. Click New in the Networks tab and select the appropriate Primary usage. 2. Click Next to continue. 110 | Authentication Dell PowerConnect W-Series Instant Access Point 6.1.3.4-3.1.0.0 | User Guide