Dell PowerConnect W-IAP92 Dell Instant 6.1.3.4-3.1.0.0 User Guide - Page 127
MAC Authentication, Configuring MAC Authentication,
 |
View all Dell PowerConnect W-IAP92 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 127 highlights
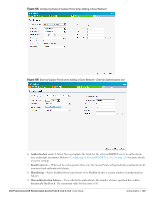
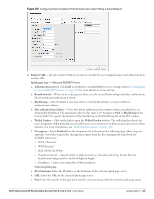
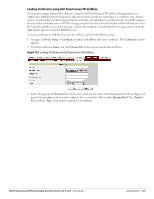
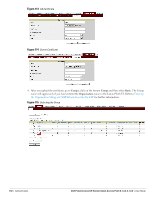
9. Login to the network with the username and password specified used while configuring the RADIUS server in step d. MAC Authentication Media Access Control (MAC) authentication is used to authenticate devices based on their physical MAC addresses. It is an early form of filtering. MAC authentication requires that the MAC address of a machine must match a manually defined list of addresses. This form of authentication does not scale past a handful of devices, because it is difficult to maintain the list of MAC addresses. Additionally, it is easy to change the MAC address of a station to match one on the accepted list. This spoofing is trivial to perform with built-in driver tools, and it should not be relied upon to provide security. MAC authentication can be used alone, but typically it is combined with other forms of authentication, such as WEP authentication. Because MAC addresses are easily observed during transmission and easily changed on the client, this form of authentication should be considered nothing more than a minor hurdle. Dell recommends against the use of MAC-based authentication. Configuring MAC Authentication To enable MAC Authentication for a wireless network: 1. In the Network tab, click the network for which you want to enable MAC authentication. The edit link for the network appears. 2. Click the edit link and navigate to the Security tab. 3. For a network with Personal or Open security level, select Enabled from the MAC Authentication drop-down list. 4. Click OK to continue. Figure 108 Configuring MAC Authentication 5. Click Next and then click Finish to apply the changes. Dell PowerConnect W-Series Instant Access Point 6.1.3.4-3.1.0.0 | User Guide Authentication | 127