Dell PowerConnect W-IAP92 Dell Instant 6.1.3.4-3.1.0.0 User Guide - Page 55
Conditions for Adding a Voice Network- Security Tab, Both WPA-2 & WPA
 |
View all Dell PowerConnect W-IAP92 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 55 highlights
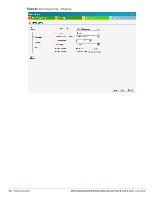
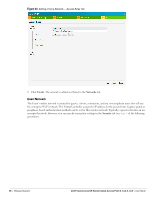
Table 9 Conditions for Adding a Voice Network- Security Tab If then, You select the Enterprise security level Perform the following steps: 1. Select the required key options from the Key management drop-down list. Available options are: WPA-2 Enterprise WPA Enterprise Both (WPA-2 & WPA) Dynamic WEP with 802.1x Use Session Key for LEAP: Use the Session Key for LEAP instead of using Session Key from the RADIUS Server to derive pair wise unicast keys. This is required for old printers that use dynamic WEP via LEAP authentication. This is Disabled by default. For more information on encryption and recommended encryption type, see Chapter 11, "Encryption" . 2. Termination- Enable this option to terminate the EAP portion of 802.1x authentication on the IAP instead of the RADIUS server. For more information, see "External RADIUS Server" on page 110. 3. Authentication server 1 and 2- Select the required Authentication server option from the drop-down list. Available options are: New- If you select this option, then an external radius server has to be configured to authenticate the users. For information on configuring an external RADIUS server, see Chapter 10, "Authentication" . 4. Reauth interval- When set to a value greater than zero, the Access Points periodically reauthenticate all associated and authenticated clients. 5. Blacklisting- Select Enabled if you want clients to be blacklisted after a certain number of authentication failures. 6. Max authentication failures- Users who fail to authenticate the number of times specified here will be dynamically blacklisted. The maximum value for this entry is 10. NOTE: Navigate to PEF > Blacklisting in the WebUI to specify the duration of the blacklisting on the Blacklisting tab of the PEF window. Dell PowerConnect W-Series Instant Access Point 6.1.3.4-3.1.0.0 | User Guide Wireless Network | 55