Dell PowerConnect W-IAP92 Dell Instant 6.1.3.4-3.1.0.0 User Guide - Page 165
Intrusion Detection System, Rogue AP Detection and Classification, Wireless Intrusion Protection (WIP)
 |
View all Dell PowerConnect W-IAP92 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 165 highlights
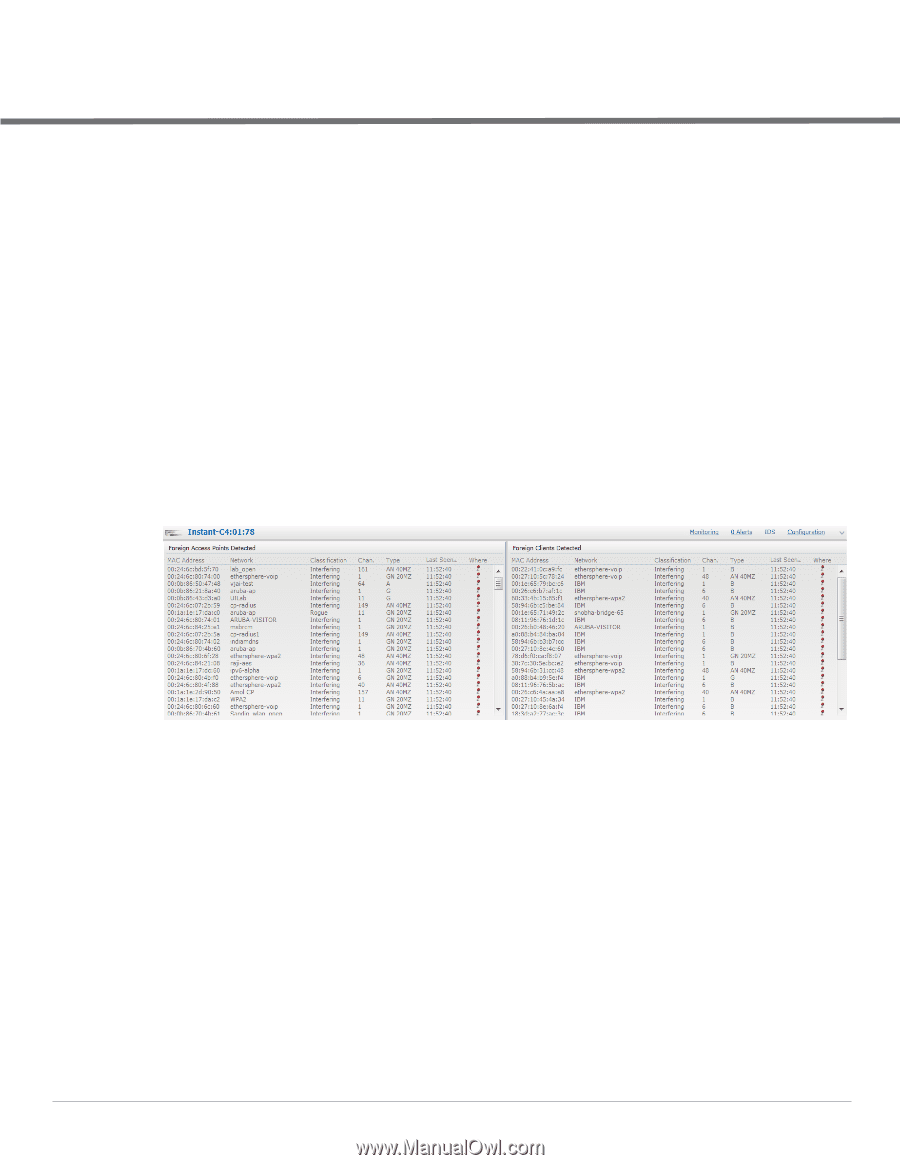
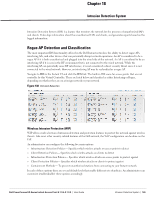
Chapter 18 Intrusion Detection System Intrusion Detection System (IDS) is a feature that monitors the network for the presence of unauthorized IAPs and clients. It also logs information about the unauthorized IAPs and clients, and generates reports based on the logged information. Rogue AP Detection and Classification The most important IDS functionality offered in the Dell Instant network is the ability to detect rogue APs, interfering APs, and other devices that can potentially disrupt network operations. An AP is considered to be a rogue AP if it is both unauthorized and plugged into the wired side of the network. An AP is considered to be an interfering AP if it is seen in the RF environment but is not connected to the wired network. While the interfering AP can potentially cause RF interference, it is not considered a direct security threat since it is not connected to the wired network. However, an interfering AP may be reclassified as a rogue AP. Navigate to IDS in the Instant UI and click the IDS link. The built-in IDS scans for access points that are not controller by this Virtual Controller. These are listed below and classified as either Interfering or Rogue, depending on whether they are on a foreign network or your network. Figure 138 Intrusion Detection Wireless Intrusion Protection (WIP) WIP offers a wide selection of intrusion detection and protection features to protect the network against wireless threats. Like most other security-related features of the Dell network, the WIP configuration can be done on the IAP. An administrator can configure the following five main options: Infrastructure Detection Policies- Specifies which wireless attacks on access points to detect Client Detection Policies- Specifies which wireless attacks on clients to detect Infrastructure Protection Policies- Specifies which wireless attacks on access points to protect against Client Protection Policies- Specifies which wireless attacks on clients to protect against Containment Methods- To prevent unauthorized stations from connecting to your Instant network. In each of these options there are several default levels that enable different sets of policies. An administrator can customize (enable/disable) these options accordingly. Dell PowerConnect W-Series Instant Access Point 6.1.3.4-3.1.0.0 | User Guide Intrusion Detection System | 165