HP 6125XLG R2306-HP 6125XLG Blade Switch Layer 3 - IP Services Configuration G - Page 165
Configuring tunneling, Overview, IPv6 over IPv4 tunneling, Implementation
 |
View all HP 6125XLG manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 165 highlights
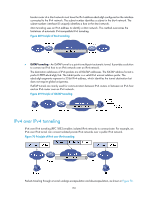
Configuring tunneling Overview Tunneling is an encapsulation technology. One network protocol encapsulates packets of another network protocol and transfers them over a virtual point-to-point connection. The virtual connection is called a tunnel. Packets are encapsulated at the tunnel source end and de-encapsulated at the tunnel destination end. Tunneling refers to the whole process from data encapsulation to data transfer to data de-encapsulation. Tunneling supports the following technologies: • Transition techniques, such as IPv6 over IPv4 tunneling, to interconnect IPv4 and IPv6 networks. • VPN, such as IPv4 over IPv4 tunneling, IPv4/IPv6 over IPv6 tunneling, GRE, DVPN, and IPsec tunneling. • Traffic engineering, such as MPLS TE to prevent network congestion. Unless otherwise specified, the term tunnel in this document refers to IPv6 over IPv4, IPv4 over IPv4, IPv4 over IPv6, and IPv6 over IPv6 tunnels. IPv6 over IPv4 tunneling Implementation IPv6 over IPv4 tunneling enables isolated IPv6 networks to communicate, as shown in Figure 67. The devices at the ends of an IPv6 over IPv4 tunnel must support the IPv4/IPv6 dual stack. Figure 67 IPv6 over IPv4 tunnel The IPv6 over IPv4 tunnel processes packets in the following steps: 1. A host in the IPv6 network sends an IPv6 packet to Device A at the tunnel source. 2. After determining according to the routing table that the packet needs to be forwarded through the tunnel, Device A encapsulates the IPv6 packet with an IPv4 header and forwards it through the physical interface of the tunnel. In the IPv4 header, the source IPv4 address is the IPv4 address of the tunnel source, and the destination IPv4 address is the IPv4 address of the tunnel destination. 3. Upon receiving the packet, Device B de-encapsulates the packet. 157