HP 6125XLG R2306-HP 6125XLG Blade Switch Layer 3 - IP Services Configuration G - Page 88
DNS configuration task list
 |
View all HP 6125XLG manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 88 highlights
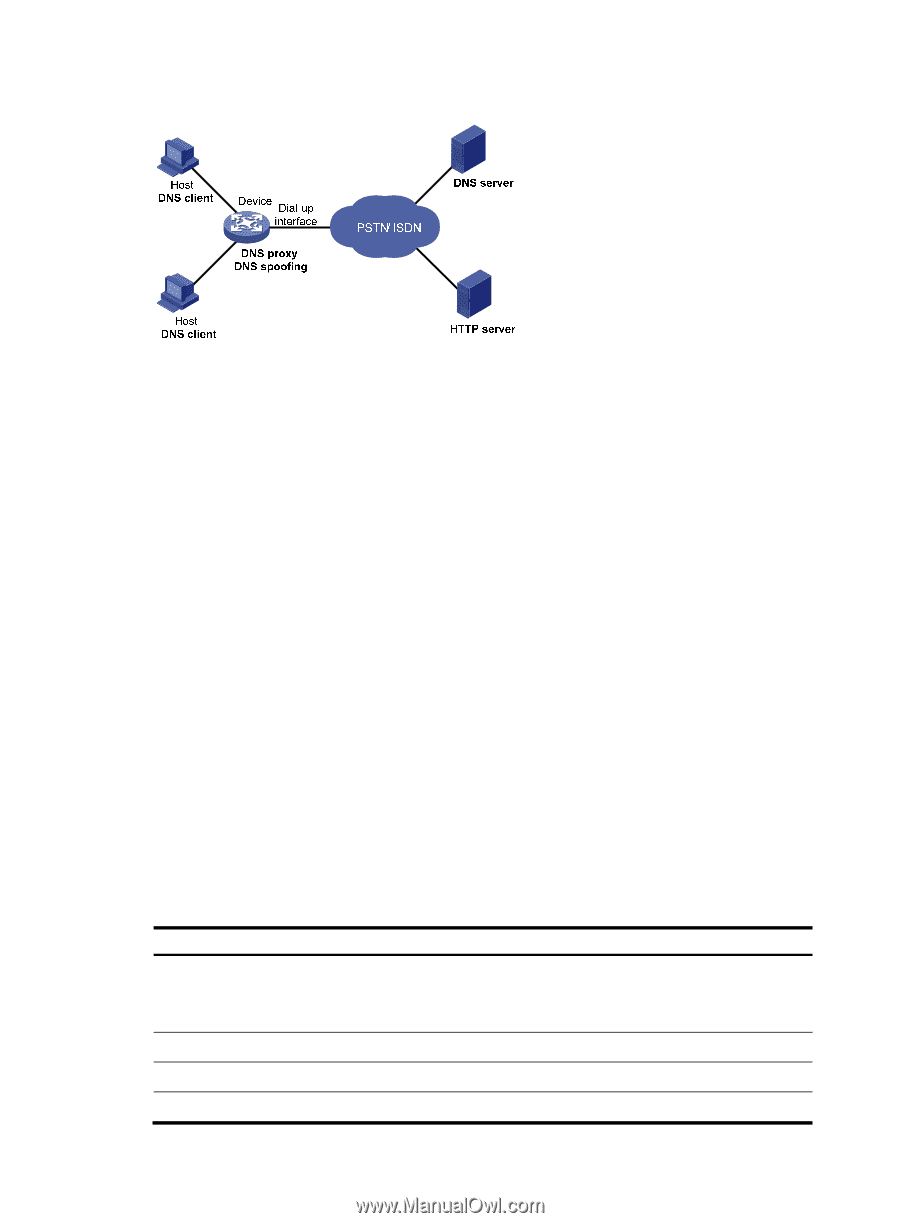
Figure 32 DNS spoofing application DNS spoofing enables the DNS proxy to send a spoofed reply with a configured IP address even if it cannot reach the DNS server. Without DNS spoofing, the proxy does not answer or forward a DNS request if it cannot find a matching DNS entry and it cannot reach the DNS server. In the network as shown in Figure 32, a host accesses the HTTP server in following these steps: 1. The host sends a DNS request to the device to resolve the domain name of the HTTP server into an IP address. 2. Upon receiving the request, the device searches the local static and dynamic DNS entries for a match. If the dial-up connection has not been established, the device does not know the DNS server address, or the DNS server address configured on the device is not reachable, the device spoofs the host by replying a configured IP address. The TTL of the DNS reply is 0. The device must have a route to the IP address with the dial-up interface as the output interface. The IP address configured with DNS spoofing is not the actual IP address of the requested domain name, so the TTL of the DNS reply is set to 0 to prevent the DNS client from generating incorrect domain name-to-IP address mappings. 3. Upon receiving the reply, the host sends an HTTP request to the replied IP address. 4. When forwarding the HTTP request through the dial-up interface, the device establishes a dial-up connection with the network, and dynamically obtains the DNS server address through DHCP or other autoconfiguration mechanisms. 5. When the DNS reply ages out, the host sends a DNS request to the device again. 6. Then the device operates the same as a DNS proxy. For more information, see "DNS proxy." 7. After obtaining the IP address of the HTTP server, the host can access the HTTP server. DNS configuration task list Tasks at a glance Perform one of the following tasks: • Configuring the IPv4 DNS client • Configuring the IPv6 DNS client (Optional.) Configuring the DNS proxy (Optional.) Configuring DNS spoofing (Optional.) Specifying the source interface for DNS packets 79