Dell PowerConnect W Clearpass 100 Software 3.9 Deployment Guide - Page 494
Optional EAP Module Options, Continued, Table 62
 |
View all Dell PowerConnect W Clearpass 100 Software manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 494 highlights
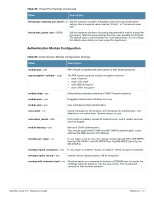
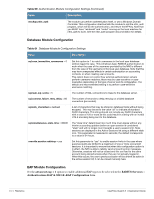
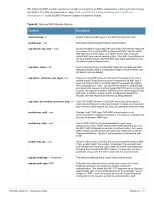
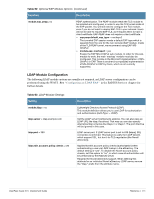
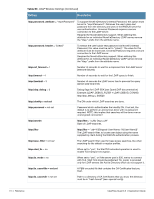
Table 62 Optional EAP Module Options (Continued) Function Description module.eap_tls = no module.eap_ttls = no Enables EAP-TLS module. The following functions onfigure digital certificates for EAP-TLS. If the private key and certificate are located in the same file, then private_key_file and certificate_file must contain the same filename. eap.tls.private_key_password = not set eap.tls.private_key_file = "${raddbdir}/certs/cert-srv.pem" eap.tls.certificate_file = "${raddbdir}/certs/cert-srv.pem" eap.tls.dh_file = "${raddbdir}/certs/dh" eap.tls.random_file = "${raddbdir}/certs/random" eap.tls.CA_file = "${raddbdir}/certs/demoCA/cacert.pem" Trusted root CA list. eap.tls.fragment_size = 1024 This can never exceed the size of a RADIUS packet (4096 bytes), and is preferably half that, to accommodate other attributes in the RADIUS packet. On most APs the maximum packet length is configured between 1500 - 1600. In these cases, fragment size should be 1024 or less. eap.tls.include_length = yes If set to yes, the total length of the message is included in every packet we send. If set to no, total length of the message is included only in the first packet of a fragment series. eap.tls.check_crl = yes Check the Certificate Revocation List. eap.tls.check_cert_cn = not set If check_cert_cn is set, the value will be xlat'ed and checked against the CN in the client certificate. If the values do not match, the certificate verification will fail, rejecting the user. The TTLS module implements the EAP-TTLS protocol, which can be described as EAP inside of Diameter, inside of TLS, inside of EAP, inside of RADIUS. The TTLS module needs the TLS module to be installed and configured, in order to use the TLS tunnel inside of the EAP packet. You will still need to configure the TLS module, even if you do not want to deploy EAP-TLS in your network. Users will not be able to request EAP-TLS, as it requires them to have a client certificate. EAP-TTLS does not require a client certificate.eap.ttls.default_eap_type = md5 The tunneled EAP session needs a default EAP type which is separate from the one for the non-tunneled EAP module. Inside of the TTLS tunnel, we recommend using EAP-MD5. If the request does not contain an EAP conversation, then this configuration entry is ignored. eap.ttls.copy_request_to_tunnel = no The tunneled authentication request does not usually contain useful attributes like Calling-Station-Id, etc. These attributes are outside of the tunnel, and are normally unavailable to the tunneled authentication request. By setting this configuration entry to 'yes', any attribute which is not in the tunneled authentication request, but which is available outside of the tunnel, is copied to the tunneled request. eap.ttls.use_tunneled_reply = no The reply attributes sent to the NAS are usually based on the name of the user 'outside' of the tunnel (usually 'anonymous'). If you want to send the reply attributes based on the username inside of the tunnel, then set this configuration entry to 'yes', and the reply to the NAS will be taken from the reply to the tunneled request. 494 | Reference ClearPass Guest 3.9 | Deployment Guide