Dell PowerConnect W Clearpass 100 Software 3.9 Deployment Guide - Page 72
Setting Up an Intermediate Certificate Authority, Clock Skew Allowance
 |
View all Dell PowerConnect W Clearpass 100 Software manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 72 highlights
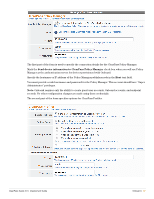
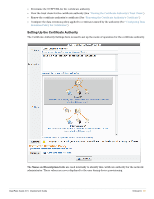
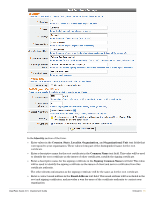
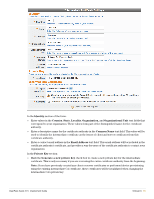
In the Private Key section: Mark the Generate a new private key check box to create a new private key for the root certificate. This is only necessary if you are recreating the entire certificate authority from the beginning. Note: If you have previously created any client or server certificates or performed device provisioning using the existing root certificate, these certificates will be invalidated when changing the root certificate's private key. The Key Type drop-down list specifies the type of private key that should be created for the certificate. You can select one of these options: 1024-bit RSA - not recommended for a root certificate 2048-bit RSA - recommended for general use 4096-bit RSA - higher security In the Self-Signed Certificate section: Use the CA Expiration field to specify the lifetime of the root certificate in days. The default value of 3653 days is a 10-year lifetime. The Clock Skew Allowance field adds a small amount of time to the start and end of the root certificate's validity period. This permits a newly issued certificate to be recognized as valid in a network where not all devices are perfectly synchronized. The Digest Algorithm drop-down list allows you to specify which hash algorithm should be used. Note: MD5 is not recommended for use with root certificates. Mark the Generate CA certificate and invalidate all other certificates check box to confirm the changes. Click the Create Root Certificate button to save the settings and generate a new root certificate. Setting Up an Intermediate Certificate Authority The Intermediate Certificate Settings form is used to configure the distinguished name and properties for the certificate authority's certificate, which will be issued by an external certificate authority. Note: If you intend to change any of the intermediate certificate's distinguished name properties, and you have previously created any client or server certificates or performed device provisioning using the existing intermediate certificate, these certificates will be invalidated as the intermediate certificate's distinguished name has changed. In this case, you should use the Reset to Factory Defaults form (see "Resetting Onboard Certificates and Configuration") to delete all client certificates and re-provision all devices. You will also need to reissue any server or subordinate CA certificates. To avoid the complication of revoking and reissuing certificates, it is recommended that you configure the certificate authority before any device provisioning or other configuration is done. 72 | Onboard ClearPass Guest 3.9 | Deployment Guide