Dell PowerConnect W Clearpass 100 Software 3.9 Deployment Guide - Page 91
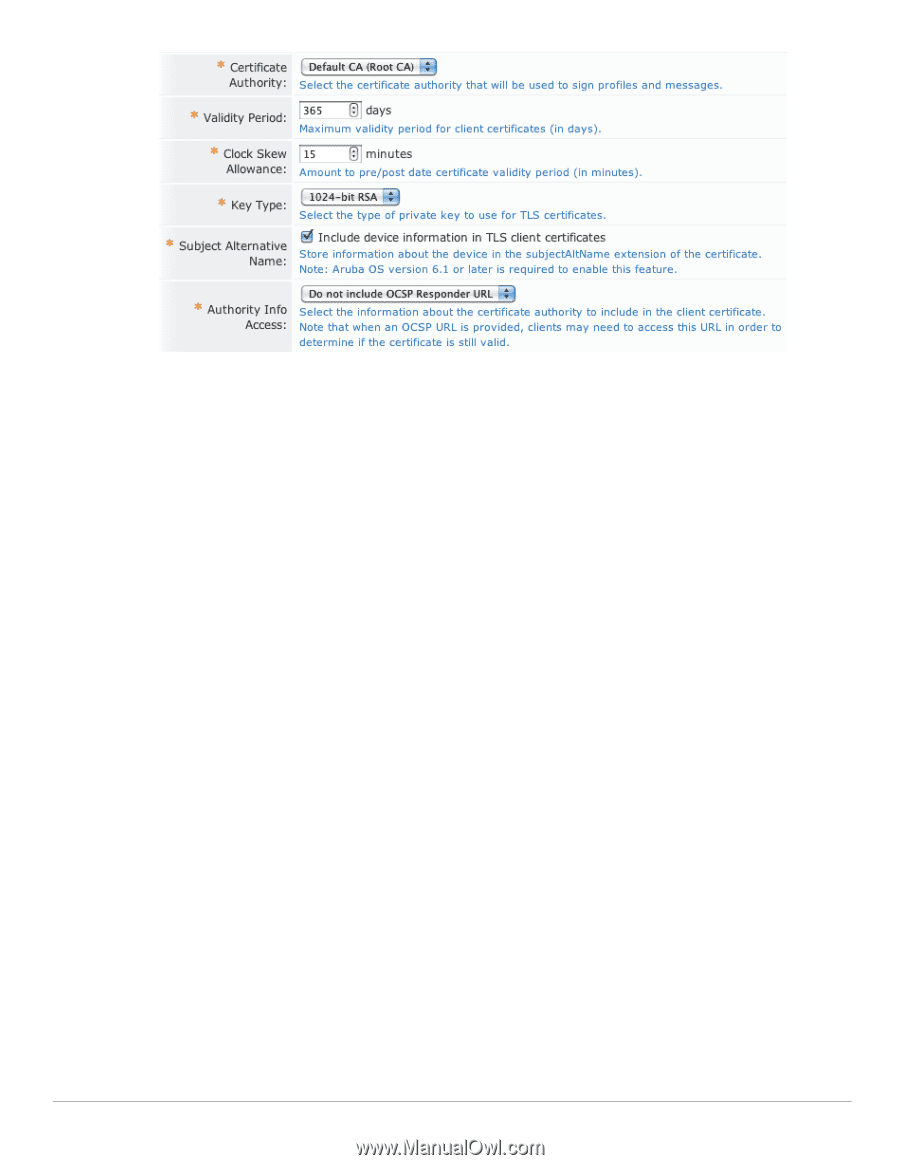
Certificate Authority, Validity Period, Clock Skew Allowance, Key Type, bit RSA
 |
View all Dell PowerConnect W Clearpass 100 Software manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 91 highlights
The Certificate Authority drop-down list can be used to select a different certificate authority. By default, there is only a single certificate authority. Use the Validity Period text field to specify the maximum length of time for which a client certificate issued during device provisioning will remain valid. The Clock Skew Allowance text field adds a small amount of time to the start and end of the client certificate's validity period. This permits a newly issued certificate to be recognized as valid in a network where not all devices are perfectly synchronized. For example, if the current time is 12:00, and the clock skew allowance is set to the default value of 15 minutes, then the client certificate will be issued with a "not valid before" time of 11:45. In this case, if the authentication server that receives the client certificate has a time of 11:58, it will still recognize the certificate as valid. If the clock skew allowance was set to 0 minutes, then the authentication server would not recognize the certificate as valid until its clock has reached 12:00. The default of 15 minutes is reasonable. If you expect that all devices on the network will be synchronized then the value may be reduced. A setting of 0 minutes is not recommended as this does not permit any variance in clocks between devices. When issuing a certificate, the certificate's validity period is determined as follows: The "not valid before" time is set to the current time, less the clock skew allowance. The "not valid after" time is first calculated as the earliest of the following: The current time, plus the maximum validity period. The expiration time of the user account for whom the device certificate is being issued. The "not valid after" time is then increased by the clock skew allowance. The Key Type drop-down list specifies the type of private key that should be created when issuing a new certificate. You can select one of these options: 1024-bit RSA - lower security 2048-bit RSA - recommended for general use 4096-bit RSA - higher security Note: Using a private key containing more bits will increase security, but will also increase the processing time required to create the certificate and authenticate the device. The additional processing required will also affect the battery life of a mobile device. It is recommended to use the smallest private key size that is feasible for your organization. ClearPass Guest 3.9 | Deployment Guide Onboard | 91