Dell PowerConnect W Clearpass 100 Software 3.9 Deployment Guide - Page 54
Revoking Credentials to Prevent Network Access, Re-Provisioning a Device, Working with Certificates
 |
View all Dell PowerConnect W Clearpass 100 Software manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 54 highlights
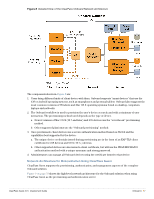
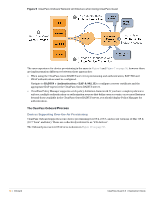
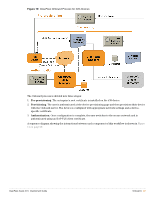
To disable network access for a device, revoke the TLS client certificate provisioned to the device. See "Working with Certificates". Note: Revoking access for a device is only possible when using an enterprise network. Personal (PSK) networks do not support this capability. Revoking Credentials to Prevent Network Access Revoking a device's certificate will also prevent the device from being re-provisioned. This is necessary to prevent the user from simply re-provisioning and obtaining a new certificate. To reprovision the device, the revoked certificate must be deleted. If the device is provisioned with an EAP-TLS client certificate, revoking the certificate will cause the certificate authority to update the certificate's state. When the certificate is next used for authentication, it will be recognized as a revoked certificate and the device will be denied access. Note: When using EAP-TLS authentication, you must configure your authentication server to use either OCSP or CRL to check the revocation status of a client certificate. OCSP is recommended as it offers a realtime status update for certificates. If the device is provisioned with PEAP unique device credentials, revoking the certificate will automatically delete the unique username and password associated with the device. When this username is next used for authentication, it will not be recognized as valid and the device will be denied access. Note: OCSP and CRL are not used when using PEAP unique device credentials. The Onboard server automatically updates the status of the username when the device's client certificate is revoked. Re-Provisioning a Device Because "bring your own" devices are not under the complete control of the network administrator, it is possible for unexpected configuration changes to occur on a provisioned device. For example, the user may delete the configuration profile containing the settings for the provisioned network, instruct the device to forget the provisioned network settings, or reset the device to factory defaults and destroy all the configuration on the device. When these events occur, the user will not be able to access the provisioned network and will need to reprovision their device. The Onboard server detects a device that is being re-provisioned and prompts the user to take a suitable action (such as connecting to the appropriate network). If this is not possible, the user may choose to restart the provisioning process and re-provision the device. Re-provisioning a device will reuse an existing TLS client certificate or unique device credentials, if these credentials are still valid. If the TLS client certificate has expired then the device will be issued a new certificate. This enables reprovisioning to occur on a regular basis. If the TLS client certificate has been revoked, then the device will not be permitted to re-provision. The revoked certificate must be deleted before the device is able to be provisioned. 54 | Onboard ClearPass Guest 3.9 | Deployment Guide