Dell PowerConnect W Clearpass 100 Software 3.9 Deployment Guide - Page 497
Setting, Description, Table 63
 |
View all Dell PowerConnect W Clearpass 100 Software manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 497 highlights
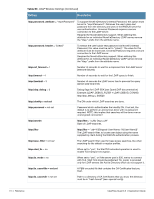
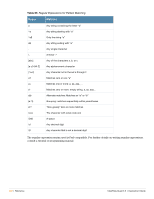
Table 63 LDAP Module Settings (Continued) Setting Description ldap.tls_certfile = not set ldap.tls_randfile = not set ldap.tls_require_cert = not set ldap.default_profile = not set ldap.profile_attribute = not set ldap.access_attrused_for_allow = yes ldap.access_attr = dialupAccess ldap.password_header = not set ldap.password_attribute = not set ldap.groupname_attribute = not set ldap.compare_check_items = no ldap.do_xlat = yes The PEM Encoded certificate file that should be presented to clients that connect. ldap.tls_keyfile = not set The PEM Encoded private key that should be used to encrypt the session. A file containing random data to seed the OpenSSL PRNG. Not needed if your OpenSSL is already properly random. Certificate Verification requirements. Can be "never" (don't even bother trying), "allow" (try, but don't fail if the certificate can't be verified), or "demand" (fail if the certificate doesn't verify). DN of a LDAP object, which contains default RADIUS attributes. If not set, use only user specific attributes or attributes, supplied by other modules. Name of a user object attribute, which contains DN of radiusProfile object for this user. If unset, use only user specific attributes or attributes, supplied by other modules. Determines if the access attribute (described below) will be used to allow access (meaning if it exists then user remote access will be allowed) or to deny access. If attribute is specified, the LDAP module checks for its existence in the user object. If access_attr_used_for_allow is set to yes, and the attribute exists, the user is allowed to get remote access. If the attribute exists and is set to FALSE, the user is denied remote access. If the attribute does not exist, the user is denied remote access by default. If access_attr_used_for_allow is set to no, and the attribute exists, the user is denied remote access. If it does not exist, the user is allowed remote access. If the user password is available we add it to the check items (to assist in CHAP), stripping any headers first. The password_header directive is NOT case insensitive. Define the attribute which contains the user password. The attribute containing group name in the LDAP server. It is used to search groups by name. Specifies if the module will do a comparison on the check items extracted from the ldap with the corresponding items present in the incoming request. Specifies if the module will do an xlat on the radius attributes extracted from the ldap database. Also, the attribute operators will be honored. If the directive is set to 'no' then we will fall back to the pairadd() function which will just add the attributes at the end of the corresponding attribute list (check or reply items). This can be used to fall back to 0.8.1 behavior without changing the LDAP data or to gain a little performance if the LDAP data is rather simple (no special operators) ClearPass Guest 3.9 | Deployment Guide Reference | 497