Dell PowerConnect W Clearpass 100 Software 3.9 Deployment Guide - Page 495
LDAP Module Configuration, LDAP Module Settings, Optional EAP Module Options, Continued
 |
View all Dell PowerConnect W Clearpass 100 Software manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 495 highlights
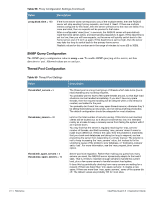
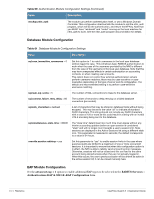
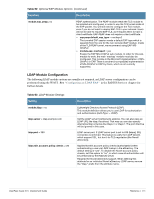
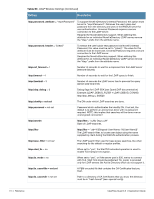
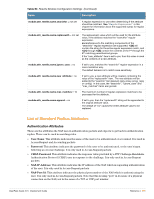
Table 62 Optional EAP Module Options (Continued) Function Description module.eap_peap= no PEAP authentication. The PEAP module needs the TLS module to be installed and configured, in order to use the TLS tunnel inside of the EAP packet. You will still need to configure the TLS module, even if you do not want to deploy EAP-TLS in your network. Users will not be able to request EAP-TLS, as it requires them to have a client certificate. EAP-PEAP does not require a client certificate. eap.peap.default_eap_type = mschapv2 The tunneled EAP session needs a default EAP type which is separate from the one for the non-tunneled EAP module. Inside of the TLS/PEAP tunnel, we recommend using EAP-MSCHAPv2. module.eap_mschapv2 = yes Enable the EAP MS-CHAPv2 sub-module. In order for this submodule to work, the main 'mschap' module must also be configured. This module is the Microsoft implementation of MSCHAPv2 in EAP. There is another (incompatible) implementation of MS-CHAPv2 in EAP by Cisco, which is not currently supported. LDAP Module Configuration The following LDAP module options are usually not required, as LDAP server configuration can be performed using the WebUI. See "Configuring an LDAP EAS" in the RADIUS Services chapter for further details. Table 63 LDAP Module Settings Setting module.ldap = no ldap.server = ldap.example.com ldap.port = 389 ldap.edir_account_policy_check = yes Description Lightweight Directory Access Protocol (LDAP). This module definition allows you to use LDAP for authorization and authentication (Auth-Type := LDAP). Set the LDAP server hostname/ip address. You can also pass an LDAP URL like ldap://localhost. That way you can also specify alternative ldap schemas like ldaps:// or ldapi://. The port directive will be ignored in this case. LDAP server port. If LDAP server port is set to 636 (ldaps), SSL connection is enforced. This feature is useful for LDAP servers which support SSL, but don't do TLS negotiation (like Novell eDirectory). Applies Novell's account policy checks (authorization) when authenticating a user via LDAP lookup in the eDirectory. The default setting is "yes". To disable the Novell account policy checks, set this option to "no", in which case all authorization will be performed by the RADIUS server. Required for Novell eDirectory support. When defining this attribute for an individual Novell eDirectory LDAP server, remove the "ldap." prefix from the attribute name. ClearPass Guest 3.9 | Deployment Guide Reference | 495