Netgear FS752TPS FS752TS Setup Manual - Page 143
Port Security, Broadcast Control, Broadcast Rate Threshold, APPLY
 |
View all Netgear FS752TPS manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 143 highlights
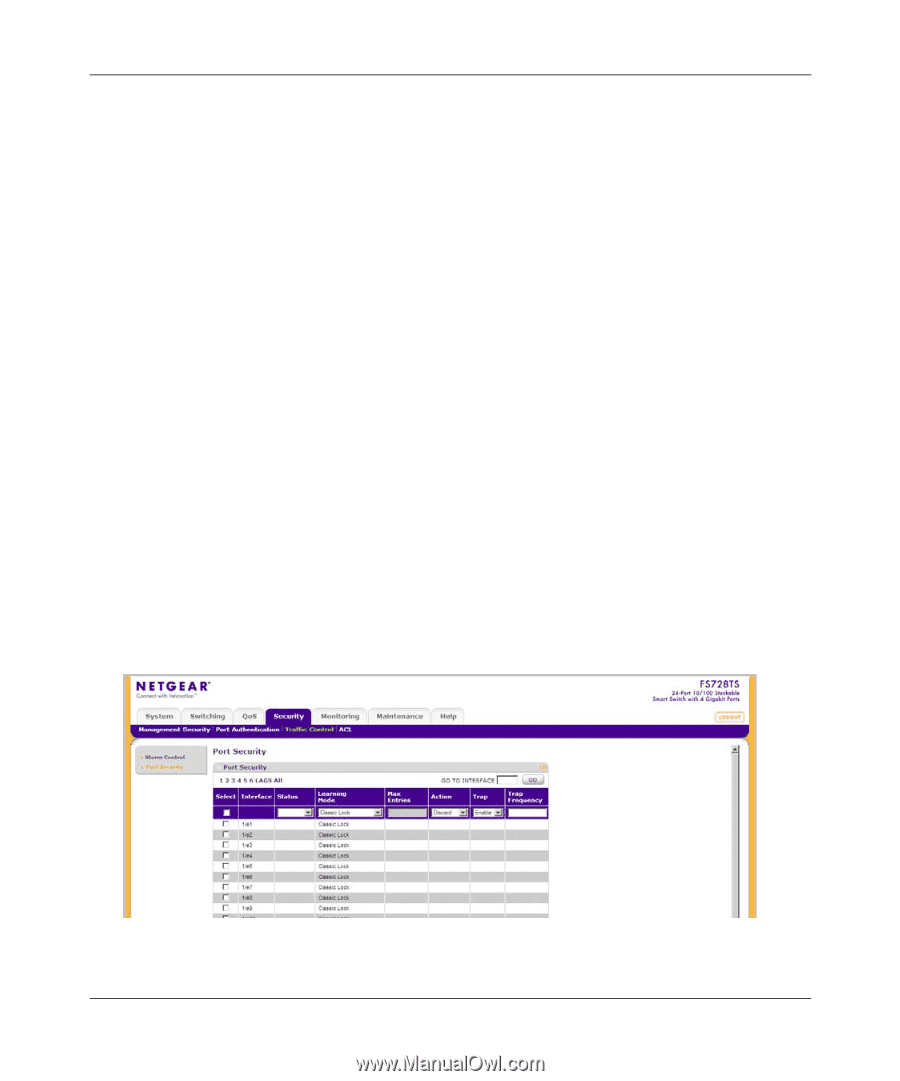
FS700TS Smart Switch Software Administration Manual 5. If you selected Enable Broadcast Control, enter the Broadcast Rate Threshold in the provided field in the first row. 6. Click APPLY to update the device. Port Security Network security can be increased by limiting access on a specific port only to users with specific MAC addresses. The MAC addresses can be dynamically learned or statically configured. Locked port security monitors both received and learned packets that are received on specific ports. Access to the locked port is limited to users with specific MAC addresses. These addresses are either manually defined on the port, or learned on that port up to the point when it is locked. When a packet is received on a locked port and the packet source MAC address is not tied to that port (either it was learned on a different port, or it is unknown to the system), the protection mechanism is invoked. It provides the following options for unauthorized packets arriving at a locked port: • Forwarded • Discarded with no trap • Discarded with a trap • Shuts down the port Locked port security also enables storing a list of MAC addresses in the configuration file. The MAC address list can be restored after the device has been reset. To define port security: 1. Click Security > Traffic Control > Port Security. The Port Security screen displays: Figure 6-9 Managing Security v1.0, September 2007 6-15