Dell PowerConnect W-IAP92 Dell Instant 6.2.0.0-3.2.0.0 User Guide - Page 179
Custom settings
 |
View all Dell PowerConnect W-IAP92 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 179 highlights
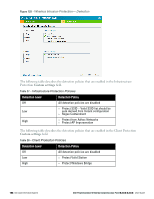
Detection Level Detection Policy l Detect Client Flood Attack l Detect Bad WEP l Detect CTS Rate Anomaly l Detect RTS Rate Anomaly l Detect Invalid Address Combination l Detect Malformed Frame- HT IE l Detect Malformed Frame- Association Request l Detect Malformed Frame- Auth l Detect Overflow IE l Detect Overflow EAPOL Key l Detect Beacon Wrong Channel l Detect devices with invalid MAC OUI The following table describes the detection policies that are enabled in the Client Detection Custom settings field. Table 26 - Client Detection Policies Detection Level Detection Policy Off All detection policies are disabled. Low Medium l Detect Valid Station Misassociation l Detect Disconnect Station Attack l Detect Omerta Attack l Detect FATA-Jack Attack l Detect Block ACK DOS l Detect Hotspotter Attack l Detect unencrypted Valid Client l Detect Power Save DOS Attack l Detect EAP Rate Anomaly l Detect Rate Anomaly High l Detect Chop Chop Attack l Detect TKIP Replay Attack l IDS Signature- Air Jack l IDS Signature- ASLEAP Three levels of detection can be configured in the WIP Protection page- Off, Low, and High (as shown in Figure 128). Dell PowerConnect W-Series Instant Access Point 6.2.0.0-3.2.0.0 | User Guide 179 | Intrusion Detection System