Dell PowerConnect W-IAP92 Dell Instant 6.2.0.0-3.2.0.0 User Guide - Page 30
PEF, WIP, Rogue AP Detection and Classification
 |
View all Dell PowerConnect W-IAP92 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 30 highlights
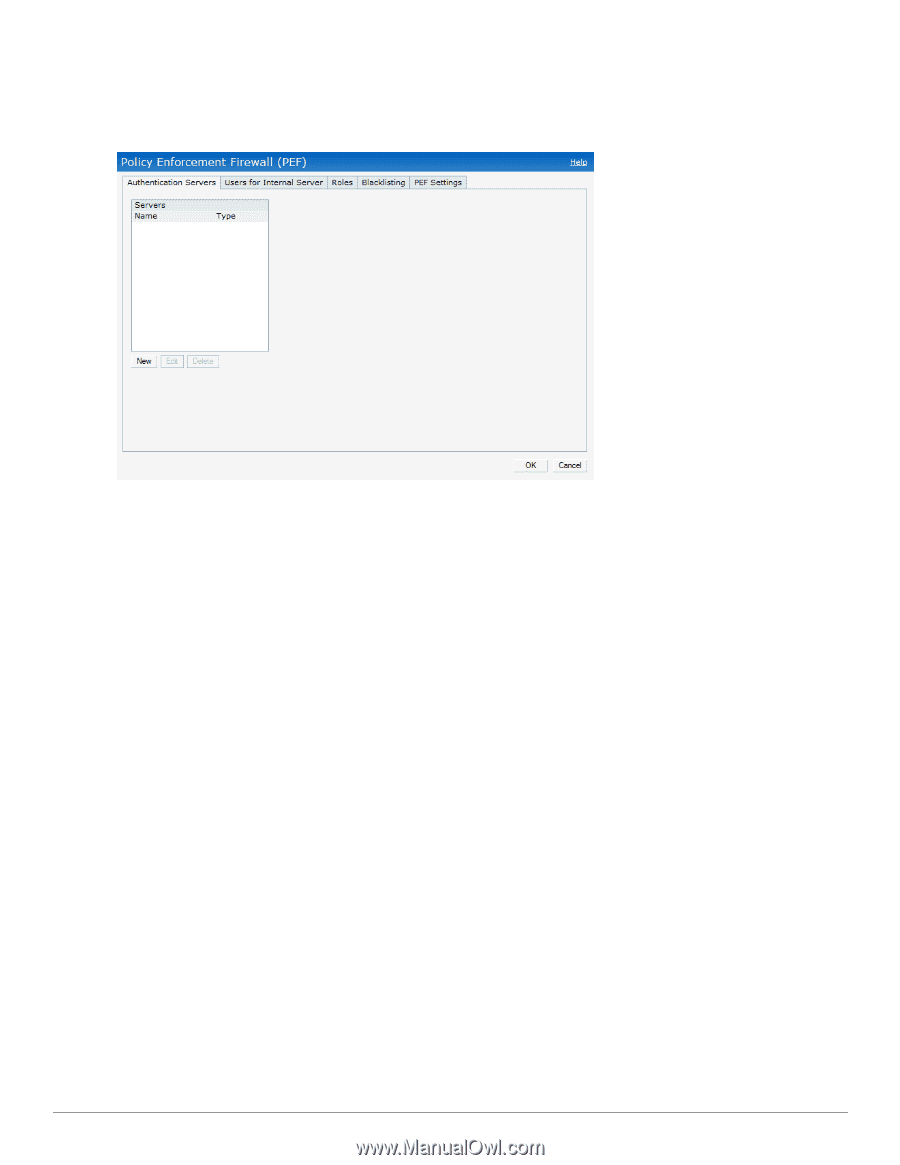
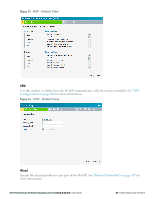
PEF This link displays the following features. Figure 12 - PEF Authentication Servers- Use this window to configure an external RADIUS server for a wireless network. See "802.1X Authentication" on page 111 for more information. Users for Internal Server- Use this window to populate the system's internal authentication server with users. This list is used by networks for which per-user authorization is specified using the Virtual Controller's internal authentication server. For more information about users, see "User Database" on page 269. Roles- This window displays all the roles defined for all the Networks. The Access Rules part indicates the permissions for each role. For more information, see "User Roles" on page 145. Blacklisting- Use this window to manually blacklist clients. See "Client Blacklisting" on page 255 for more information. Policy Enforcement Firewell (PEF) Settings- Use this window to enable/disable Application Layer Gateway (ALG) supporting address and port translation for various protocols. See "Policy Enforcement Firewall" on page 251 for more information. WIP Wireless Intrusion Protection (WIP) offers a wide selection of intrusion detection and protection features to protect the network against wireless threats. Use this window to specify desired levels of threat detection. See "Rogue AP Detection and Classification" on page 177 for more information. 30 | Dell W-Instant User Interface Dell PowerConnect W-Series Instant Access Point 6.2.0.0-3.2.0.0 | User Guide