Netgear GS110TP GS108Tv2/GS110TP Software Reference Manual - Page 221
IP Extended Rule, Assign Queue ID, Match Every, Source IP Address, Source IP Mask, Delete, Apply
 |
UPC - 606449069129
View all Netgear GS110TP manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 221 highlights
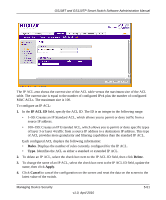
GS108T and GS110TP Smart Switch Software Administration Manual • Assign Queue ID. Specifies the hardware egress queue identifier used to handle all packets matching this ACL rule. Enter an identifying number from 0-3 in the appropriate field. • Match Every. Requires a packet to match the criteria of this ACL. Select True or False from the drop down menu. Match Every is exclusive to the other filtering rules, so if Match Every is True, the other rules on the screen are not available. • Source IP Address. Requires a packet's source IP address to match the address listed here. Type an IP Address in the appropriate field using dotted-decimal notation. The address you enter is compared to a packet's source IP Address. • Source IP Mask. Specifies the source IP address wildcard mask. Wild card masks determines which bits are used and which bits are ignored. A wild card mask of 255.255.255.255 indicates that no bit is important. A wildcard of 0.0.0.0 indicates that all of the bits are important. Wildcard masking for ACLs operates differently from a subnet mask. A wildcard mask is in essence the inverse of a subnet mask. For example, to apply the rule to all hosts in the 192.168.1.0/24 subnet, you type 0.0.0.255 in the Source IP Mask field. This field is required when you configure a source IP address. 2. To delete an IP ACL rule, select the check box associated with the rule, and then click Delete. 3. To update an IP ACL rule, select the check box associated with the rule, update the desired fields, and then click Apply. You cannot modify the Rule ID of an existing IP rule. 4. Click Cancel to cancel the configuration on the screen and reset the data on the screen to the latest value of the switch. 5. If you change any of the settings on the page, click Apply to send the updated configuration to the switch. Configuration changes take effect immediately. IP Extended Rule Use the IP Extended Rules page to define rules for IP-based extended ACLs. The access list definition includes rules that specify whether traffic matching the criteria is forwarded normally or discarded. Note: There is an implicit "deny all" rule at the end of an ACL list. This means that if an ACL is applied to a packet and if none of the explicit rules match, then the final implicit "deny all" rule applies and the packet is dropped. To display the IP extended Rules page, click Security ACL, then click the Advanced IP Extended Rules link. Managing Device Security v1.0, April 2010 5-53