Intel S2600CP Technical Product Specification - Page 68
Trusted Platform Module TPM Support - base system device
 |
View all Intel S2600CP manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 68 highlights
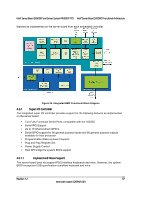
System Security Intel® Server Board S2600CP and Server System P4000CP TPS new USB boot device is attached to the system. A User is restricted from booting in anything other than the Boot Order defined in the Setup by an Administrator. As a security measure, if a User or Administrator enters an incorrect password three times in a row during the boot sequence, the system is placed into a halt state. A system reset is required to exit out of the halt state. This feature makes it more difficult to guess or break a password. In addition, on the next successful reboot, the Error Manager displays a Major Error code 0048, which also logs a SEL event to alert the authorized user or administrator that a password access failure has occurred 5.2 Trusted Platform Module (TPM) Support The Trusted Platform Module (TPM) option is a hardware-based security device that addresses the growing concern on boot process integrity and offers better data protection. TPM protects the system start-up process by ensuring it is tamper-free before releasing system control to the operating system. A TPM device provides secured storage to store data, such as security keys and passwords. In addition, a TPM device has encryption and hash functions. The server board implements TPM as per TPM PC Client Specifications revision 1.2 by the Trusted Computing Group (TCG). A TPM device is optionally installed onto a high density 14-pin connector labeled "TPM" on the server board, and is secured from external software attacks and physical theft. A pre-boot environment, such as the BIOS and operating system loader, uses the TPM to collect and store unique measurements from multiple factors within the boot process to create a system fingerprint. This unique fingerprint remains the same unless the pre-boot environment is tampered with. Therefore, it is used to compare to future measurements to verify the integrity of the boot process. After the system BIOS completes the measurement of its boot process, it hands off control to the operating system loader and in turn to the operating system. If the operating system is TPMenabled, it compares the BIOS TPM measurements to those of previous boots to make sure the system was not tampered with before continuing the operating system boot process. Once the operating system is in operation, it optionally uses TPM to provide additional system and data security (for example, Microsoft Vista* supports Bitlocker drive encryption). 5.2.1 TPM security BIOS The BIOS TPM support conforms to the TPM PC Client Implementation Specification for Conventional BIOS and to the TPM Interface Specification, and the Microsoft Windows BitLocker* Requirements. The role of the BIOS for TPM security includes the following: Measures and stores the boot process in the TPM microcontroller to allow a TPM enabled operating system to verify system boot integrity. Produces EFI and legacy interfaces to a TPM-enabled operating system for using TPM. Produces ACPI TPM device and methods to allow a TPM-enabled operating system to send TPM administrative command requests to the BIOS. Verifies operator physical presence. Confirms and executes operating system TPM administrative command requests. 52 Revision 1.2 Intel order number G26942-003