Intel S2600CP Technical Product Specification - Page 71
Intel, Trusted Execution Technology
 |
View all Intel S2600CP manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 71 highlights
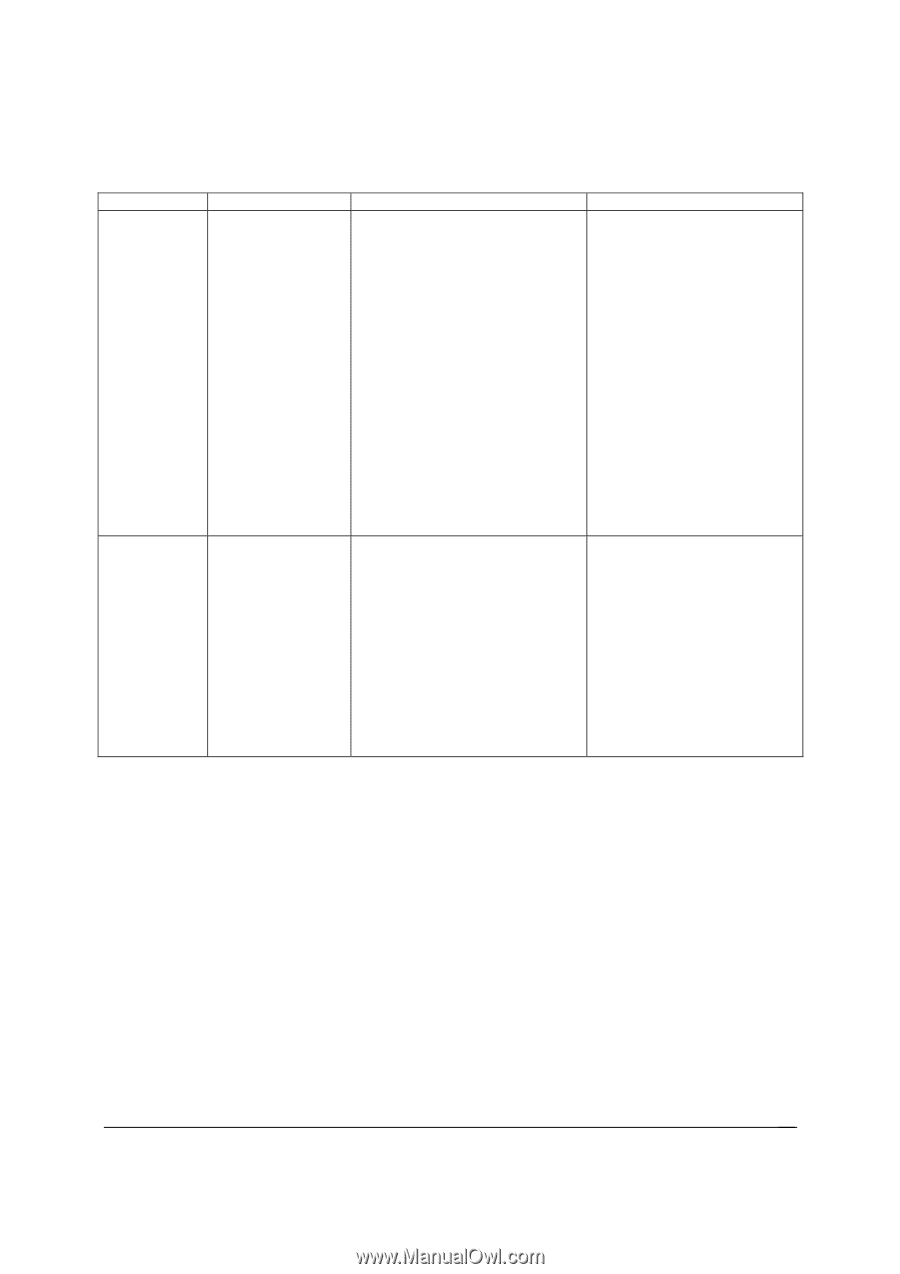
Intel® Server Board S2600CP and Server System P4000CP TPS System Security Setup Item TPM State* Table 13. TSetup Utility - Security Configuration Screen Fields Options Enabled and Activated Enabled and Deactivated Disabled and Activated Disabled and Deactivated Help Text Comments Information only. Shows the current TPM device state. A disabled TPM device will not execute commands that use TPM functions and TPM security operations will not be available. An enabled and deactivated TPM is in the same state as a disabled TPM except setting of TPM ownership is allowed if not present already. TPM Administrative Control** No Operation Turn On Turn Off Clear Ownership [No Operation] - No changes to current state. [Turn On] - Enables and activates TPM. [Turn Off] - Disables and deactivates TPM. [Clear Ownership] - Removes the TPM ownership authentication and returns the TPM to a factory default state. Note: The BIOS setting returns to [No Operation] on every boot cycle by default. An enabled and activated TPM executes all commands that use TPM functions and TPM security operations will be available. 5.3 Intel® Trusted Execution Technology The Intel® Xeon® Processor E5-2600 support Intel® Trusted Execution Technology (Intel® TXT), which is a robust security environment. Designed to help protect against software-based attacks, Intel® Trusted Execution Technology integrates new security features and capabilities into the processor, chipset and other platform components. When used in conjunction with Intel® Virtualization Technology, Intel® Trusted Execution Technology provides hardware-rooted trust for your virtual applications. This hardware-rooted security provides a general-purpose, safer computing environment capable of running a wide variety of operating systems and applications to increase the confidentiality and integrity of sensitive information without compromising the usability of the platform. Intel® Trusted Execution Technology requires a computer system with Intel® Virtualization Technology enabled (both VT-x and VT-d), an Intel® Trusted Execution Technology-enabled processor, chipset and BIOS, Authenticated Code Modules, and an Intel® Trusted Execution Revision 1.2 55 Intel order number G26942-003