Intel S2600CP Technical Product Specification - Page 89
LAN Interface
 |
View all Intel S2600CP manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 89 highlights
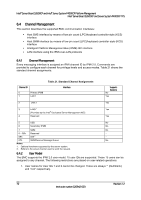
Intel® Server Board S2600CP and Server System P4000CP TPS Intel® Server Board S2600CP and Intel® Server System P4000CP Platform Management 2. User 2 ("root") always has the administrator privilege level. 3. All user passwords (including passwords for 1 and 2) may be modified. 4. User IDs 3-15 may be used freely, with the condition that user names are unique. Therefore, no other users can be named "" (Null), "root," or any other existing user name. 6.4.3 LAN Interface The BMC implements both the IPMI 1.5 and IPMI 2.0 messaging models. These provide out-ofband local area network (LAN) communication between the BMC and the network. Run-time determination of LAN channel capabilities can be determined by both standard IPMI defined mechanisms. 6.4.3.1 IPMI 1.5 Messaging The communication protocol packet format consists of IPMI requests and responses encapsulated in an IPMI session wrapper for authentication, and wrapped in an RMCP packet, which is wrapped in an IP/UDP packet. Although authentication is provided, no encryption is provided, so administrating some settings, such as user passwords, through this interface is not advised. Session establishment commands are IPMI commands that do not require authentication or an associated session. The BMC supports the following authentication types over the LAN interface. 1. None (no authentication) 2. Straight password/key 3. MD5 6.4.3.2 IPMI 2.0 Messaging IPMI 2.0 messaging is built over RMCP+ and has a different session establishment protocol. The session commands are defined by RMCP+ and implemented at the RMCP+ level, not IPMI commands. Authentication is implemented at the RMCP+ level. RMCP+ provides link payload encryption, so it is possible to communicate private/sensitive data (confidentiality). The BMC supports the cipher suites identified in Table 22. Table 22. Supported RMCP+ Cipher Suites ID Authentication Algorithm 01 RAKP-none 1 RAKP-HMAC-SHA1 2 RAKP-HMAC-SHA1 3 RAKP-HMAC-SHA1 6 RAKP-HMAC-MD5 7 RAKP-HMAC-MD5 8 RAKP-HMAC-MD5 11 RAKP-HMAC-MD5 Integrity Algorithm(s) None None HMAC-SHA1-96 HMAC-SHA1-96 None HMAC-MD5-128 HMAC-MD5-128 MD5-128 Confidentiality Algorithm(s) None None None AES-CBC-128 None None AES-CBC-128 None Revision 1.2 73 Intel order number G26942-003