McAfee MIS09EMB3RAA User Guide - Page 64
Personal Firewall features
 |
UPC - 731944575278
View all McAfee MIS09EMB3RAA manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 64 highlights
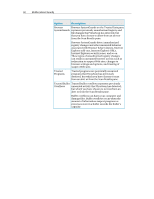
62 McAfee Internet Security Personal Firewall features Standard and custom protection levels Guard against intrusion and suspicious activity using Firewall's default or customizable protection settings. Real-time recommendations Intelligent access management for programs Receive recommendations, dynamically, to help you decide whether programs should be allowed Internet access or network traffic should be trusted. Manage Internet access for programs, through alerts and event logs, and configure access permissions for specific programs. Gaming protection Computer startup protection Prevent alerts regarding intrusion attempts and suspicious activities from distracting you during full-screen gameplay. Protect your computer from intrusion attempts, unwanted programs and network traffic as soon as Windows® starts. System service port control Manage open and closed system service ports required by some programs. Manage computer connections Allow and block remote connections between other computers and your computer. HackerWatch information integration Lockdown Firewall Restore Firewall Track global hacking and intrusion patterns through HackerWatch's Web site, which also provides current security information about programs on your computer, as well as global security events and Internet port statistics. Block all inbound and outbound traffic instantly between your computer and the Internet. Restore Firewall's original protection settings instantly. Advanced Trojan detection Event logging Detect and block potentially malicious applications, such as Trojans, from sending your personal data to the Internet. Track recent inbound, outbound, and intrusion events. Monitor Internet traffic Intrusion prevention Sophisticated traffic analysis Review worldwide maps showing the source of hostile attacks and traffic. In addition, locate detailed owner information and geographical data for originating IP addresses. Also, analyze inbound and outbound traffic, monitor program bandwidth and program activity. Protect your privacy from possible Internet threats. Using heuristic-like functionality, we provide a tertiary layer of protection by blocking items that display symptoms of attacks or characteristics of hacking attempts. Review both inbound and outbound Internet traffic and program connections, including those that are actively listening for open connections. This allows you to see and act upon programs that can be vulnerable to intrusion.