D-Link DGS-3130 User Manual - Page 310
Network Access Authentication Sessions Information
 |
View all D-Link DGS-3130 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 310 highlights
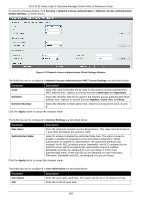
DGS-3130 Series Layer 3 Stackable Managed Switch Web UI Reference Guide Parameter CompAuth Mode Description the client is authenticated, the client will not be re-authenticated when received from other VLANs. This option is useful for trunk ports to do per-VLAN authentication control. When a port's authentication mode is changed to multihost, the previous authentication VLAN(s) on this port will be cleared. Select the compound authentication mode option here. Options to choose from are Any and MAC-WAC. Selecting Any specifies that if any of the authentication method (802.1X, MAC-based Access Control or WAC) to passes, then pass. Selecting MAC-WAC specifies to verify MAC-based authentication first. If the client passes, WAC will be verified next. Both authentication methods need to be passed. Max Users Periodic ReAuth Timer Inactivity State Inactivity Timer Restart Enter the maximum users value used here. This value must be between 1 and 1000. Select to enable or disable periodic re-authentication for the selected port here. This parameter only affects the 802.1X protocol. Enter the re-authentication timer value here. This value must be between 1 and 65535 seconds. By default, this value is 3600 seconds. Select to enable or disable the inactivity state here. Select the Time option to enable this feature. When the Inactivity State is enabled, enter the inactivity timer value here. This value must be between 120 and 65535 seconds. This parameter only affects the WAC authentication protocol. Enter the restart time value used here. This value must be between 1 and 65535 seconds. Click the Apply button to accept the changes made. Network Access Authentication Sessions Information This window is used to view and clear the network access authentication session information. To view the following window, click Security > Network Access Authentication > Network Access Authentication Sessions Information, as shown below: Figure 9-76 Network Access Authentication Sessions Information Window The fields that can be configured are described below: 300