Intel SE7525GP2 Product Specification - Page 131
Secure Mode Operation
 |
View all Intel SE7525GP2 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 131 highlights
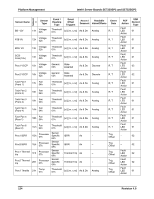
Intel® Server Boards SE7320SP2 and SE7525GP2 Platform Management on-Critical Condition ƒ Temperature, voltage, or fan non-critical threshold crossing ƒ Chassis intrusion ƒ Satellite controller sends a non-critical state, via the Set Fault Indication command, to the mBMC ƒ Set Fault Indication command from system BIOS. The BIOS may use the Set Fault Indication command to indicate additional, non-critical status such as system memory or CPU configuration changes. Degraded Condition ƒ One or more processors are disabled by Fault Resilient Boot (FRB) or BIOS ƒ BIOS has disabled or mapped out some of the system memory 5.3.4.6 Chassis Intrusion Switch Some platforms support chassis intrusion detection. On these platforms, the mBMC monitors the state of the Chassis Intrusion signal and makes the status of the signal available via the Get Chassis Status command and Physical Security sensor state. If enabled, a chassis intrusion state change causes the mBMC to generate a Physical Security sensor event message with a General Chassis Intrusion offset. 5.3.4.7 Front Panel Lockout The management controller monitors a 'Secure Mode' signal from the keyboard controller on the server board. When the Secure Mode signal is asserted, the management controller may lock out the ability to power down or reset the system using the power or reset push buttons, respectively. Secure Mode may also block the ability to initiate a sleep request using the sleep push-button. The management controller generates a 'Secure Mode Violation Attempt' event message if an attempt it made to power-down, sleep, or reset the system using the push buttons while Secure Mode is active. The mBMC will prevent the system from powering up via button press when either secure mode or the front panel lockout I/O signal is asserted. 5.3.5 Secure Mode Operation Secure mode is a signal from the SIO/keyboard controller. Power and reset buttons are locked out, except for the NMI and Chassis ID buttons. A security violation event is generated if buttons are pressed while secure mode active. The Secure Mode feature allows the front panel switches and other system resources to be protected against unauthorized use or access. Secure Mode is enabled and controlled via the Set Secure Mode Options command. Revision 4.0 119