Intel SE7525GP2 Product Specification - Page 132
FRU Information
 |
View all Intel SE7525GP2 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 132 highlights
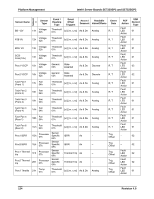
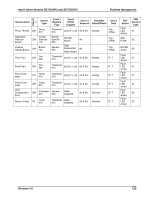
Platform Management Intel® Server Boards SE7320SP2 and SE7525GP2 If it is enabled, Secure Mode can be controlled via the Secure Mode KB signal from the keyboard controller. When Secure Mode is active, pressing a protected front panel switch generates a Secure Mode Violation event. Specifically, this generates an assertion of the Secure Mode Violation Attempt offset of the mBMC's Platform Security Violation Attempt sensor. The Secure Mode state is cleared whenever AC power or system power is applied, when a system reset occurs, or when a mBMC reset occurs. The Secure Mode state includes the bits that specify the actions that are to be taken when Secure Mode is active, as well as the Force Secure Mode On bit. The Set Secure Mode Options command allows specific front panel switches to be protected irrespective of Secure Mode state. See the command definition in the IPMI v1.5 specification for details. The NMI switch can be locked using the Set Secure Mode Options command but is never protected by Secure Mode. This allows a system to be recovered from a hung state when Secure Mode is active 5.3.6 FRU Information The platform management architecture supports providing FRU (field replaceable unit) information for the server board and major replaceable modules in the chassis. 'Major Module' is defined as any circuit board in the system containing active electronic circuitry. FRU information includes board serial number, part number, name, asset tag, and other information. FRUs that contain a management controller use the controller to provide access to the FRU information. FRUs that lack a management controller can make their FRU information available via a SEEPROM directly connected to the IPMB or a private I2C bus. This allows the system integrator to provide a chassis FRU device without having to implement a management controller. This information can be accessed via IPMI FRU commands or using Master WriteRead commands. The mBMC implements the interface for logical FRU inventory devices as specified in the Intelligent Platform Management Interface Specification, Version 1.5. This functionality provides commands used for accessing and managing the FRU inventory information associated with the mBMC (FRU ID 0). These commands can be delivered via all interfaces. 5.3.6.1 mBMC FRU Inventory Area Format The mBMC FRU inventory area format follows the Platform Management FRU Information Storage Definition. Refer to Platform Management FRU Information Storage Definition, Version 1.0 for details. The mBMC provides only low-level access to the FRU inventory area storage. It does not validate or interpret the data that are written. This includes the common header area. Applications cannot relocate or resize any FRU inventory areas. The server board's FRU information is kept in the mBMC internal flash memory. 120 Revision 4.0