Netgear SRX5308 SRX5308 Reference Manual - Page 191
Table 5-16. Add IKE Policy Settings for a Mode Config Configuration continued, Remote
 |
UPC - 606449065145
View all Netgear SRX5308 manuals
Add to My Manuals
Save this manual to your list of manuals |
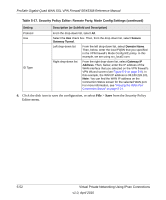
Page 191 highlights
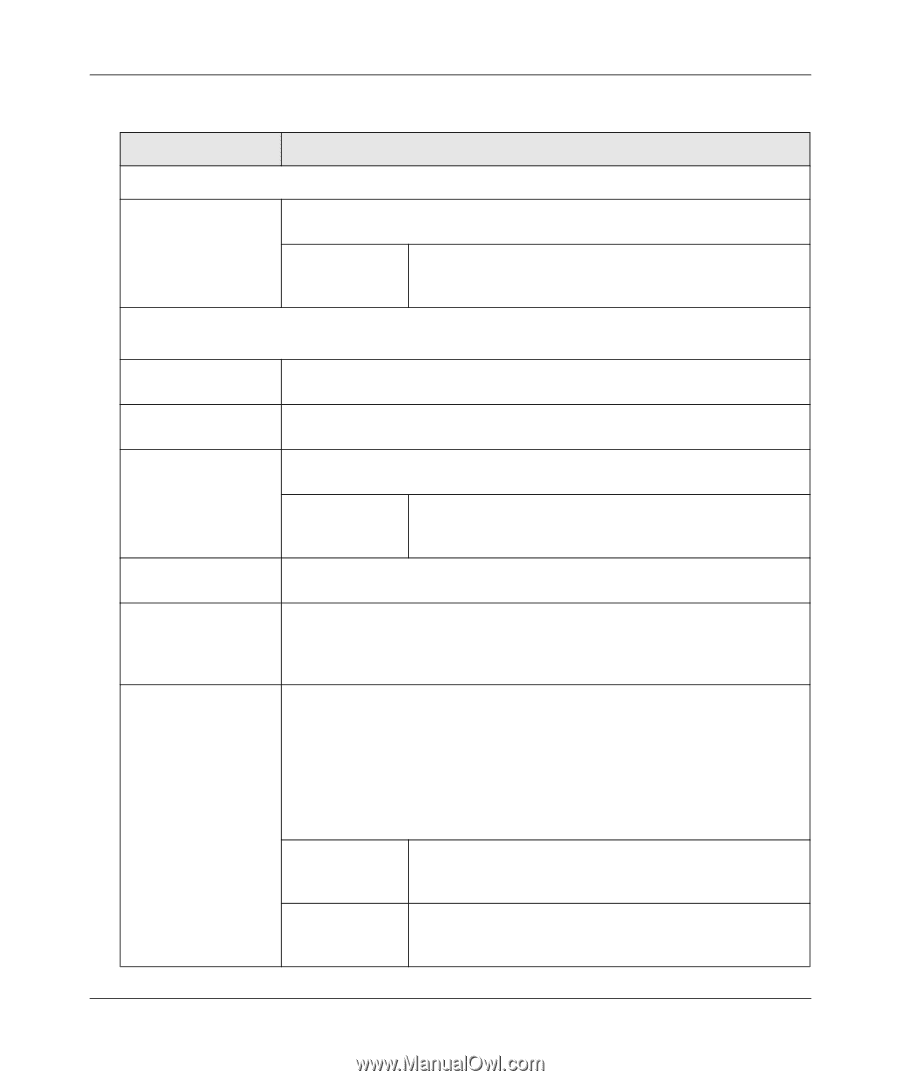
ProSafe Gigabit Quad WAN SSL VPN Firewall SRX5308 Reference Manual Table 5-16. Add IKE Policy Settings for a Mode Config Configuration (continued) Item Description (or Subfield and Description) Remote Identifier Type From the drop-down list, select FQDN. Note: Mode Config requires that the remote end is defined by an FQDN. Identifier Enter the FQDN for the remote end. This must be an FQDN that is not used in any other IKE policy. In this example, we are using srx_remote2.com. IKE SA Parameters Note: Generally, the default settings work well for a Mode Config configuration. Encryption Algorithm From the drop-down list, select the 3DES algorithm to negotiate the security association (SA). Authentication Algorithm From the drop-down list, select the SHA-1 algorithm to be used in the VPN header for the authentication process. Authentication Method Select Pre-shared key as the authentication method, and enter a key in the Pre-shared key field. Pre-shared key A key with a minimum length of 8 characters and no more than 49 characters. Do not use a double quote (") in the key. In this example, we are using 12345678910. Diffie-Hellman (DH) Group The DH Group sets the strength of the algorithm in bits. From the drop-down list, select Group 2 (1024 bit). SA-Lifetime (sec) The period in seconds for which the IKE SA is valid. When the period times out, the next rekeying must occur. The default is 28800 seconds (8 hours). However, for a Mode Config configuration, NETGEAR recommends 3600 seconds (1 hour). Enable Dead Peer Detection Note: See also "Configuring Keepalives and Dead Peer Detection" on page 5-55. Select a radio button to specify whether or not Dead Peer Detection (DPD) is enabled: • Yes. This feature is enabled. When the VPN firewall detects an IKE connection failure, it deletes the IPsec and IKE SA and forces a reestablishment of the connection. You must specify the detection period in the Detection Period field and the maximum number of times that the VPN firewall attempts to reconnect in the Reconnect after failure count field. • No. This feature is disabled. This is the default setting. Detection Period The period in seconds between consecutive "DPD R-U-THERE" messages, which are sent only when the IPsec traffic is idle. The default setting is 10 seconds. Reconnect after failure count The maximum number of DPD failures before the VPN firewall tears down the connection and then attempts to reconnect to the peer. The default is 3 failures. Virtual Private Networking Using IPsec Connections v1.0, April 2010 5-49