Netgear SRX5308 SRX5308 Reference Manual - Page 213
Configuring the Client IP Address Range, SSL VPN, SSL VPN Client
 |
UPC - 606449065145
View all Netgear SRX5308 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 213 highlights
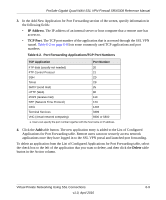
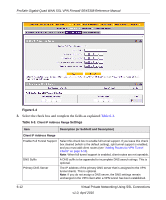
ProSafe Gigabit Quad WAN SSL VPN Firewall SRX5308 Reference Manual The following are some additional considerations: • So that the virtual (PPP) interface address of a VPN tunnel client does not conflict with addresses on the local network, configure an IP address range that does not directly overlap with addresses on your local network. For example, if 192.168.1.1 through 192.168.1.100 are currently assigned to devices on the local network, then start the client address range at 192.168.1.101 or choose an entirely different subnet altogether. • The VPN tunnel client cannot contact a server on the local network if the VPN tunnel client's Ethernet interface shares the same IP address as the server or the VPN firewall (for example, if your PC has a network interface IP address of 10.0.0.45, then you cannot contact a server on the remote network that also has the IP address 10.0.0.45). • Select whether you want to enable full tunnel or split tunnel support based on your bandwidth: - A full tunnel sends all of the client's traffic across the VPN tunnel. - A split tunnel sends only traffic that is destined for the local network based on the specified client routes. All other traffic is sent to the Internet. A split tunnel allows you to manage bandwidth by reserving the VPN tunnel for local traffic only. • If you enable split tunnel support and you assign an entirely different subnet to the VPN tunnel clients from the subnet that is used by the local network, you must add a client route to ensure that a VPN tunnel client connects to the local network over the VPN tunnel. Configuring the Client IP Address Range First determine the address range to be assigned to VPN tunnel clients, then define the address range. To define the client IP address range: 1. Select VPN > SSL VPN from the menu. The SSL VPN submenu tabs display, with the Policies screen in view. 2. Click the SSL VPN Client submenu tab. The SSL VPN Client screen displays (see Figure 6-4 on page 6-12). Virtual Private Networking Using SSL Connections v1.0, April 2010 6-11