Netgear SRX5308 SRX5308 Reference Manual - Page 261
For information about how to enable the DMZ port
 |
UPC - 606449065145
View all Netgear SRX5308 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 261 highlights
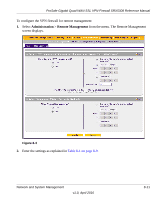
ProSafe Gigabit Quad WAN SSL VPN Firewall SRX5308 Reference Manual For information about how to enable the DMZ port, see "Configuring and Enabling the DMZ Port" on page 3-20. For the procedures on how to configure DMZ traffic rules, see "Setting DMZ WAN Rules" on page 4-14. Configuring Exposed Hosts Specifying an exposed host allows you to set up a computer or server that is available to anyone on the Internet for services that you have not yet defined. For an example of how to set up an exposed host, see "LAN WAN or DMZ WAN Inbound Rule: Specifying an Exposed Host" on page 4-24. Configuring VPN Tunnels The VPN firewall supports up to 125 site-to-site IPsec VPN tunnels and up to 50 dedicated SSL VPN tunnels. Each tunnel requires extensive processing for encryption and authentication, thereby increasing traffic through the WAN ports. For information about IPsec VPN tunnels, see Chapter 5, "Virtual Private Networking Using IPsec Connections." For information about SSL VPN tunnels, see Chapter 6, "Virtual Private Networking Using SSL Connections." Using QoS and Bandwidth Assignment to Shift the Traffic Mix By specifying QoS and bandwidth profiles and assigning these profiles to outbound and inbound firewall rules, you can shift the traffic mix to aim for optimum performance of the VPN firewall. Assigning QoS Profiles The QoS profile settings determine the priority and, in turn, the quality of service for the traffic passing through the VPN firewall. After you have created a QoS profile, you can assign the QoS profile to firewall rules. The QoS is set individually for each service. You can change the mix of traffic through the WAN ports by granting some services a higher priority than others: • You can accept the default priority defined by the service itself by not changing its QoS setting. • You can change the priority to a higher or lower value than its default setting to give the service higher or lower priority than it otherwise would have. For more information about QoS profiles, see "Creating Quality of Service (QoS) Profiles" on page 4-34. Network and System Management 8-7 v1.0, April 2010