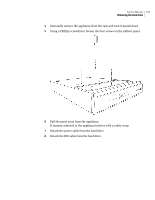
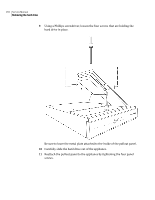
Symantec 10521148 Implementation Guide - Page 205
Domain Name Service., Smart Agent
 |
View all Symantec 10521148 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 205 highlights
Index 3 in monitored networks 108 cloning protection policy 119 clusters 41 changing IP in 103, 156 failover group in 104 initial config using CF 146 monitoring group in 103 nodes in 102 restoring configuration to 141 with ManHunt 181 compact flash. See CF compliance 188 configuration 1U 18 2U 19 CF 83 hardware 17 initial 23, 67 initial serial 25 master node, LCD 69 master node, serial 77 monitoring 29 saving 170 slave node, LCD 72 slave node, serial 80 console.See Network Security console; serial console copper gigabit on bypass unit 36 ports 35 correlation 127 crossover cable 15, 176 with bypass unit 37, 52, 60 D database force synchronization 125 last synchronization time 132 log rotation 139 monitored networks 109, 112, 114 network topology 101 synchronization 104 default gateway 70 mode for interfaces 30 deleting custom policies 123 interfaces 105 IP address from logging criteria 123 predefined policies 116 response rule 126 sample monitored network 108 to change model number 105 unapply policies before 124 denial of service. See DoS deployment bypass unit 35 cluster 41 console 42 enterprise 10 fail-open 35 flexible bandwidth 30 in-line mode 31, 33 LiveUpdate 43 passive mode 30 SESA 42 Smart Agent 42 detection 10 architecture 10 in-line mode 31 passive mode 30 starting 115 DHCP 174, 175 dimensions of appliances 185 DNS server 105, 161 documentation about the set of 13 about this guide 11 on Web 14 Domain Name Service. See DNS DoS attacks 9, 10 duplex 38 E editing /etc/hosts file 161 advanced network fields 104, 106 custom policies 120 in-line pair 111 interface group 112, 113 interface name 107 master node sync password 104 model number 103 monitored networks 109