D-Link DWS-3160-24TC DWS-3160 Series Web UI Reference Guide - Page 437
Managed SSID
 |
View all D-Link DWS-3160-24TC manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 437 highlights
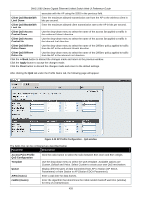
DWS-3160 Series Gigabit Ethernet Unified Switch Web UI Reference Guide Figure 3-36 WIDS Security AP Configuration window The fields that can be configured or displayed are described below: Parameter Description Administrator configured rogue AP Managed SSID from an unknown AP Managed SSID from a fake managed AP AP without an SSID Fake managed AP on an invalid channel Managed SSID detected with incorrect security Invalid SSID from a managed AP If the source MAC address is in the valid-AP database on the switch or on the RADIUS server and the AP type is marked as Rogue, then the AP state is Rogue. Select Enabled to check whether an unknown AP is using the managed network SSID. A hacker may set up an AP with managed SSID to fool users into associating with the AP and revealing password and other secure information. Administrators with large networks who are using multiple clusters should either use different network names in each cluster or disable this test. Otherwise, if an AP in the first cluster detects APs in the second cluster transmitting the same SSID as APs in the first cluster then these APs are reported as rogues. A hacker may set up an AP with the same MAC address as one of the managed APs and configure it to send one of the managed SSIDs. This test checks for a vendor field in the beacons which is always transmitted by managed APs. If the vendor field is not present, then the AP is identified as a fake AP. SSID is an optional field in beacon frames. To avoid detection a hacker may set up an AP with the managed network SSID, but disable SSID transmission in the beacon frames. The AP would still send probe responses to clients that send probe requests for the managed SSID fooling the clients into associating with the hacker's AP. This test detects and flags APs that transmit beacons without the SSID field. The test is automatically disabled if any of the radios in the profiles are configured not to send SSID field, which is not recommended because it does not provide any real security and disables this test. Select Enabled to detect rogue APs that transmit beacons from the source MAC address of one of the managed APs, but on different channel from which the AP is supposed to be operating. During RF Scan, the AP examines beacon frames received from other APs and determines whether the detected AP is advertising an open network, WEP, or WPA. If the SSID reported in the RF Scan is one of the managed networks and its configured security not match the detected security then this test marks the AP as rogue. Select Enabled to check whether a known managed AP is sending an unexpected SSID. The SSID reported in the RF Scan is compared to the list of all configured SSIDs that are used by the profile assigned to the managed AP. If the detected SSID doesn't match any configured SSID then the AP is marked as rogue. 432