D-Link DWS-3160-24TC DWS-3160 Series Web UI Reference Guide - Page 438
Standalone AP with, Rogue Detected Trap
 |
View all D-Link DWS-3160-24TC manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 438 highlights
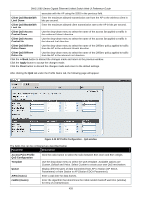
DWS-3160 Series Gigabit Ethernet Unified Switch Web UI Reference Guide AP is operating on an illegal channel Select Enabled to detect hackers or incorrectly configured devices that are operating on channels that are not legal in the country where the wireless system is set up. NOTE: In order for the wireless system to detect this threat, the wireless network must contain one or more radios that operate in sentry mode. Standalone AP with unexpected configuration If the AP is classified as a known standalone AP, the switch checks whether the AP is operating with the expected configuration parameters. You configure the expected parameters for the standalone AP in the local or RADIUS Valid AP database. Unmanaged AP detected on wired network Select Enabled to check whether the AP is detected on the wired network. If the AP state is Unknown, then the test changes the AP state to Rogue. The flag indicating whether AP is detected on the wired network is reported as part of the RF Scan report. If AP is managed and is detected on the network then the switch simply reports this fact and doesn't change the AP state to Rogue. In order for the wireless system to detect this threat, the wireless network must contain one or more radios that operate in sentry mode. Rogue Detected Trap Interval(60-3600 seconds or 0 is disable) Enter the interval, in seconds, between transmissions of the SNMP trap telling the administrator that rogue APs are present in the RF Scan database. Enter 0 to disable the function. Wired Network Detection Interval(13600 seconds or 0 is disable) Enter the number of seconds that the AP waits before starting a new wired network detection cycle. Enter 0 to disable the function. AP De-authentication Attach Select to enable or disable the AP de-authentication attack. The wireless switch can protect against rogue APs by sending de-authentication messages to the rogue AP. The de-authentication attack feature must be globally enabled in order for the wireless system to do this function. Make sure that no legitimate APs are classified as rogues before enabling the attack feature. This feature is disabled by default. Click the Apply button to accept the changes made. After clicking the Client Configuration tab, the following page will appear: Figure 3-37 WIDS Security Client Configuration window The fields that can be configured are described below: Parameter Description 433