Netgear M5300-52G3 Web Management User Guide - Page 383
Denial of Service TCP FIN & URG & PSH, Denial of Service TCP SYN & FIN
 |
View all Netgear M5300-52G3 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 383 highlights
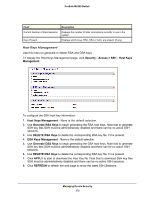
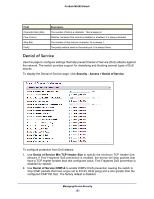
ProSafe M5300 Switch 3. Use Denial of Service Max ICMP Packet Size to specify the Max ICMPv4 Packet Size allowed (This includes the ICMP header size of 8 bytes). If ICMP DoS prevention is enabled, the switch will drop ICMP ping packets that have a size greater then this configured Max ICMP Packet Size minus the ICMP header size of 8 bytes. The factory default is 512. 4. Use Denial of Service ICMPv6 to enable ICMPv6 DoS prevention causing the switch to drop ICMP packets that have a type set to ECHO_REQ (ping) and a size greater than the configured ICMP Pkt Size. The factory default is disabled. 5. Use Denial of Service Max ICMPv6 Packet Size to specify the Max ICMPv4 Packet Size allowed (This includes the ICMP header size of 8 bytes). If ICMP DoS prevention is enabled, the switch will drop ICMP ping packets that have a size greater then this configured Max ICMP Packet Size minus the ICMP header size of 8 bytes. The factory default is 512. 6. Use Denial of Service First Fragment to enable First Fragment DoS prevention causing the switch to check DoS options on first fragment IP packets when switch are receiving fragmented IP packets. Otherwise, switch ignores the first fragment IP packages. The factory default is disabled. 7. Use Denial of Service ICMP Fragment to cause the switch to drop ICMP Fragmented packets. The factory default is disabled. 8. Use Denial of Service SIP=DIP to enable SIP=DIP DoS prevention causing the switch to drop packets that have a source IP address equal to the destination IP address. The factory default is disabled. 9. Enable Denial of Service SMAC=DMAC to cause the switch to drop packets where the source MAC address = Destination MAC address. 10. Enable Denial of Service TCP FIN & URG & PSH to cause the switch to crop packets where the TCP Flags FIN and URG and PSH set and TCP Sequence Number = 0. 11. Enable Denial of Service TCP Flag & Sequence to cause the switch to drop packets where the TCP Flag SYN set and Source Port < 1024 or TCP Control Flags = 0 and TCP Sequence Number = 0 or TCP Flags FIN, URG, and PSH set and TCP Sequence Number = 0 or TCP Flags SYN and FIN set. 12. Enable Denial of Service TCP Fragment to allow the switch to drop packets that have a TCP payload where the IP payload length minus the IP header size is less than the minimum allowed TCP header size.The factory default is disabled. 13. Enable Denial of Service TCP Offset to cause the switch to drop packets where the TCP Header Offset = 1. 14. Enable Denial of Service TCP Port to cause the switch to drop packets where the TCP source port equal to TCP destination port. The factory default is disabled. 15. Enable Denial of Service TCP SYN to cause the switch to drop packets where the TCP Flag SYN set. 16. Enable Denial of Service TCP SYN & FIN to cause the switch to drop packets where the TCP Flags SYN and FIN set. 17. Enable Denial of Service UDP Port to cause the switch to drop packets that have UDP source port equal to UDP destination port. The factory default is disabled. 18. Click APPLY to update the switch with the new settings. 19. CLick CANCEL to abandon the changes. Managing Device Security 383