Netgear M5300-52G3 Web Management User Guide - Page 416
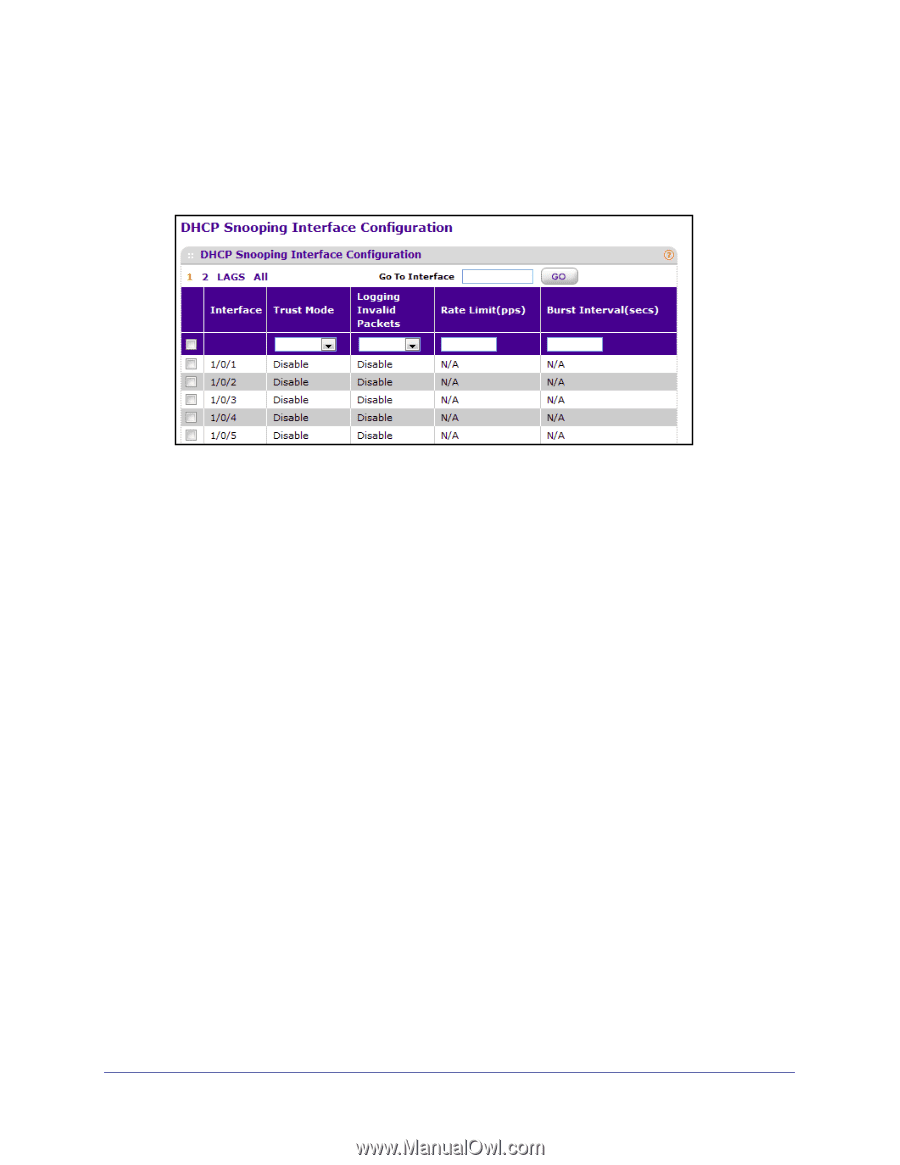
DHCP Snooping Interface Configuration, Security, Control> DHCP, Snooping, Interface Configuration.
 |
View all Netgear M5300-52G3 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 416 highlights
ProSafe M5300 Switch DHCP Snooping Interface Configuration To display the DHCP Snooping Interface Configuration page, click Security Control> DHCP Snooping Interface Configuration. To configure interfaces for DHCP snooping: 1. Select the check box associated with each interface to configure. To apply the same settings to all interfaces, select the check box in the header row. 2. If Trust Mode is enabled, DHCP snooping application considers as port trusted. DHCP servers must be reached through trusted ports.The factory default is disabled. If the trust mode is disabled (untrusted), DHCP snooping enforces the following security rules: • DHCP packets from a DHCP server (DHCPOFFER, DHCPACK, DHCPNAK, DHCPRELEASEQUERY) are dropped if they are received on an untrusted port. • DHCPRELEASE and DHCPDECLINE messages are dropped if the MAC addresses in the snooping database, but the binding's interface is other than the interface where the message was received. • On untrusted interfaces, the switch drops DHCP packets with a source MAC address that does not match the client hardware address if MAC Address Validation is globally enabled. 3. If Logging Invalid Packets is enabled, DHCP snooping application logs invalid packets on this interface. The factory default is disabled. 4. Use Rate Limit (pps) to specify rate limit value for DHCP Snooping purpose. If the incoming rate of DHCP packets exceeds the value of this object for consecutively burst interval seconds, the port will be shutdown. If this value is None there is no limit. The factory default is 15pps (packets per second). The range of Rate Limit is (0 to 300). 5. Use Burst Interval (secs) to specify the burst interval value for rate limiting purpose on this interface. If the rate limit is None burst interval has no meaning shows it as N/A. The factory default is 1 second. The range of Burst Interval is 1 to 15). 6. Click APPLY to apply the new configuration and cause the changes to take effect. These changes will not be retained across a power cycle unless a save configuration is performed. 7. Click CANCEL to abandon the changes. Managing Device Security 416