Cisco SA520-K9 Administration Guide - Page 187
IPv6 Logging, Administration, > Logging > IPv6 Logging, Accepted Packets, LAN to WAN
 |
UPC - 882658266744
View all Cisco SA520-K9 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 187 highlights
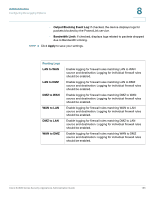
Administration Configuring the Logging Options 8 IPv6 Logging This page allows enabling logging rules for IPv6 traffic logging. STEP 1 Click Administration > Logging > IPv6 Logging. The IPV6 Logging window opens. STEP 2 Check the box for each logging option that you want to enable, or uncheck the box to disable the specified logging option. • Accepted Packets: This logs packets that were successfully transferred through the segment. This option is useful when the Default Outbound Policy is "Block Always" (see the Firewall Rules page under the Firewall menu). For example, let's say that you want a record of every successful SSH connection from the LAN to the WAN. You would check the LAN to WAN box under Accepted Packets. Whenever a LAN machine makes an SSH connection to the WAN, a message is logged. (This example assumes that your default outbound policy is "Block Always" and you have enabled a firewall rule to allow SSH traffic from the LAN to the WAN. The firewall rule also must allow logging. For more information, see Configuring Firewall Rules to Control Inbound and Outbound Traffic, page 103.) • Dropped Packets: Logs packets that were blocked from being transferred through the segment. This option is useful when the Default Outbound Policy is "Allow Always" (see the Firewall Rules page under the Firewall menu). For example, let's say that you want a record of every blocked SSH connection from the LAN to the WAN. You would check the LAN to WAN box under Dropped Packets. Whenever a machine on the LAN attempts to make an SSH connection to the WAN, a message is logged. This example assumes that your default outbound policy is "Allow Always" and you have enabled a firewall rule to block SSH traffic from the LAN to the WAN. The firewall rule also must allow logging. For more information, see Configuring Firewall Rules to Control Inbound and Outbound Traffic, page 103. STEP 3 Click Apply to save your settings. Cisco SA500 Series Security Appliances Administration Guide 187