Cisco SA520-K9 Administration Guide - Page 29
Scenario 6: Firewall for Controlling Inbound and Outbound, Traffic
 |
UPC - 882658266744
View all Cisco SA520-K9 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 29 highlights
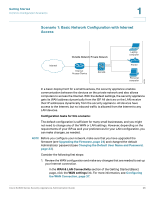
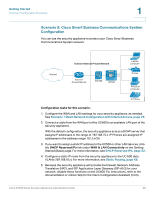
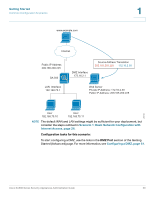
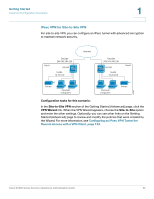
Getting Started Common Configuration Scenarios 1 Scenario 6: Firewall for Controlling Inbound and Outbound Traffic By default, all outbound traffic is allowed and all inbound traffic is denied. If you want to deny some outbound traffic or allow some inbound traffic, you will need to configure a firewall rule. To prevent unwanted traffic from the Internet, and to ensure that your employees are using the Internet for approved business purposes, you can configure various levels of firewall rules. You can configure rules that apply to a specified IP address, a range of IP addresses, or to everyone globally. Consider the following examples of firewall rules: • Block outbound traffic to certain websites • Restrict Internet access for certain users • Allow inbound traffic to your DMZ • Configure advanced NAT routing For these scenarios and all situations in which you need an exception from the default firewall policy, you need to configure firewall rules. NOTE The default WAN and LAN settings might be sufficient for your deployment, but consider the steps outlined in Scenario 1: Basic Network Configuration with Internet Access, page 26. Configuration tasks for this scenario: To start configuring your firewall rules, use the Firewall and NAT Rules links on the Getting Started (Advanced) page. For more information, see Configuring Firewall Rules to Control Inbound and Outbound Traffic, page 103. Scenario 7: DMZ for Public Websites and Services If your business hosts public services such as websites, you need a way to allow access to those services without exposing your LAN. You can address this concern by configuring the Optional port of the security appliance for use as a DMZ (Demarcation Zone or Demilitarized Zone). This zone acts as a separate network between your private LAN and the Internet. After you configure your DMZ, you can configure the firewall rules that enable traffic to connect only to the services that you specify. Cisco SA500 Series Security Appliances Administration Guide 29