D-Link DGS-3200-10 Product Manual - Page 140
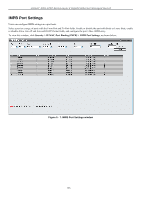
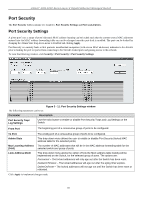
Parameter, Description, From Port/To Port, State, Allow Zero IP, SLT 0-500, Enabled Strict
 |
UPC - 790069306310
View all D-Link DGS-3200-10 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 140 highlights
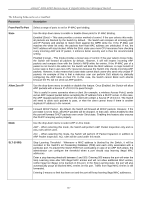
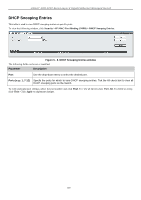
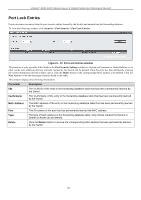
xStack® DGS-3200 Series Layer 2 Gigabit Ethernet Managed Switch The following fields can be set or modified: Parameter Description From Port/To Port Select a range of ports to set for IP-MAC-port binding. State Use the drop-down menu to enable or disable these ports for IP-MAC Binding. Enabled (Strict) - This state provides a stricter method of control. If the user selects this mode, all packets are blocked by the Switch by default. The Switch will compare all incoming ARP and IP Packets and attempt to match them against the IMPB white list. If the IP-MAC pair matches the white list entry, the packets from that MAC address are unblocked. If not, the MAC address will stay blocked. While the Strict state uses more CPU resources from checking every incoming ARP and IP packet, it enforces better security and is thus the recommended setting. Enabled (Loose) - This mode provides a looser way of control. If the user selects loose mode, the Switch will forward all packets by default. However, it will still inspect incoming ARP packets and compare them with the Switch's IMPB white list entries. If the IP-MAC pair of a packet is not found in the white list, the Switch will block the MAC address. A major benefit of Loose state is that it uses less CPU resources because the Switch only checks incoming ARP packets. However, it also means that Loose state cannot block users who send only unicast IP packets. An example of this is that a malicious user can perform DoS attacks by statically configuring the ARP table on their PC. In this case, the Switch cannot block such attacks because the PC will not send out ARP packets. Allow Zero IP Use the drop-down menu to enable or disable this feature. Once Enabled, the Switch will allow ARP packets with a Source IP of 0.0.0.0 to pass through. This is useful in some scenarios when a client (for example, a wireless Access Point,) sends out an ARP request packet before accepting the IP address from a DHCP server. In this case, the ARP request packet sent out from the client will contain a Source IP of 0.0.0.0. The Switch will need to allow such packets to pass, or else the client cannot know if there is another duplicate IP address in the network. FDP Forward DHCP Packet - By default, the Switch will forward all DHCP packets. However, if the port state is set to Strict, all DHCP packets will be dropped. In that case, select Enabled so that the port will forward DHCP packets even under Strict state. Enabling this feature also ensures that DHCP snooping works properly. Mode Use the drop-down menu to select ARP or ACL mode. ARP - When selecting this mode, the Switch will perform ARP Packet Inspection only and no ACL rules will be used. ACL - When selecting this mode, the Switch will perform IP Packet Inspection in addition to ARP Packet Inspection. ACL rules will be used under this mode. SLT (0-500) Stop Learning Threshold - Whenever a MAC address is blocked by the Switch, it will be recorded in the Switch's L2 Forwarding Database (FDB) and each entry associated with a particular port. To prevent the Switch FDB from overloading in case of an ARP DoS attack, the administrator can configure the threshold when a port should stop learning illegal MAC addresses. Enter a stop learning threshold between 0 and 500. Entering 500 means the port will enter the Stop Learning state after 500 illegal MAC entries and will not allow additional MAC entries, neither legal nor illegal, to be learned on this port. In the Stop Learning state, the port will also automatically purge all blocked MAC entries on this port. Traffic from legal MAC entries is still forwarded. Entering 0 means no limit has been set and the port will keep learning illegal MAC addresses. 127