D-Link DGS-3200-10 Product Manual - Page 159
SSL Settings, Key Exchange, Encryption, Hash Algorithm
 |
UPC - 790069306310
View all D-Link DGS-3200-10 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 159 highlights
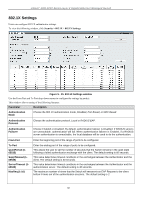
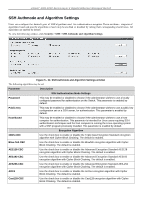
xStack® DGS-3200 Series Layer 2 Gigabit Ethernet Managed Switch SSL Settings Secure So ckets Layer, or SSL, is a security featu re t hat will provide a secu re co mmunication path b etween a host an d clien t through the use of authentication, digital signatures and encryption. These security functions are implemented through the use of a cyphersuite, which is a security string that determines the exact cryptographic parameters, specific encryption algorithms and key sizes to be used for an authentication session and consists of three levels: 1. Key Exchange: The first part of the cyphersuite string specifies the public key algorithm to be used. This switch utilizes the Rivest Shamir Adleman (RSA) public key algorithm and the Digital Signature Algorithm (DSA), specified here as the DHE DSS Diffie-Hellman (DHE) public key algorithm. This is th e first authentication process between client and host as they "exchange keys" in lookin g for a m atch and the refore authentication t o be accepted to ne gotiate encryptions on the following level. 2. Encryption: The sec ond part of t he ciphers uite th at in cludes th e en cryption used for en crypting th e m essages sen t between client and host. The Switch supports two types of cryptology algorithms: Stream Ciphers - There are two types of stream ciphers on the Switch, RC4 with 40-bit keys and RC4 with 128-bit keys. These keys are used to encrypt messages and need to be consistent between client and host for optimal use. CBC Blo ck Ci phers - CBC refers to Ciph er Blo ck C haining, which means t hat a portion of t he previously en crypted block of encrypted text is used in the encryption of the current block. The Switch supports the 3DES EDE encryption code defined by the Data Encryption Standard (DES) to create the encrypted text. 3. Hash Algorithm: This part of the ciphersuite allows the user to choose a message digest function which will determine a Message Authentication Code. Th is Messag e Au thentication C ode will b e en crypted with a sen t messag e to provide integrity and prevent against replay attacks. The Switch supports two hash algorithms, MD5 (Message Digest 5) and SHA (Secure Hash Algorithm). These three parameters are uniquely assemble d in four choices on the Sw itch to create a three-layered encryption code for secure communication between the server and the host. The user m ay implement any one or combination of the ciphersuites available, yet different ciphersuites will affect the security level and the performance of the secured connection. The information included in the ciphersuites is no t included with the Switch and requires downloading from a t hird source in a f ile form called a certificate. This function of th e Switch canno t be execu ted wit hout th e pres ence and im plementation of th e certificate file and can be downloaded to the Switch by utilizing a TFTP serv er. The Switch supports SSLv3. Other versions of SSL may not be compatible with this Switch and may cause problems upon authentication and transfer of messages from client to host. The SSL S ettings window located on the next page will allow the user to enable SSL on the Switch and implement any one or combination of listed ciph ersuites on th e Switch. A ci phersuite is a security stri ng that d etermines th e ex act cryp tographic parameters, specific encry ption algorithm s and key si zes to be use d for an a uthentication sessi on. T he S witch possesses f our possible ciph ersuites fo r t he SSL fu nction, wh ich are al l en abled by d efault. To utilize a p articular cip hersuite, d isable th e unwanted ciphersuites, leaving the desired one for authentication. When t he SSL fu nction ha s been e nabled, t he web wi ll becom e di sabled. To m anage t he S witch t hrough t he web based management wh ile utilizing th e SSL function, th e web browser m ust su pport SSL encryp tion and t he header of th e URL m ust begin with https://. (Ex. https://xx.xx.xx.xx) Any other method will result in an error and no access can be authorized for the webbased management. Users can download a certif icate file fo r the SSL function on the Switch from a TFTP server. The certificate file is a data rec ord used for authenticating devices on the network. It contains information on the owner, keys for authentication and digital signatures. Both the server and the client must have consistent certificate files fo r optimal use of the SSL function. The Switch only supports certificate files with .d er file extensions. Currently, the Switch comes with a certificate pre-loaded though the user may need to download more, depending on user circumstances. 146