D-Link DGS-3200-10 Product Manual - Page 84
Private VLAN Settings, Private VLAN domain, Port Type, Description, Promiscuous
 |
UPC - 790069306310
View all D-Link DGS-3200-10 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 84 highlights
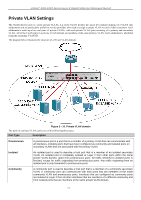
xStack® DGS-3200 Series Layer 2 Gigabit Ethernet Managed Switch Private VLAN Settings The Switch al lows users to create private VLA Ns. A p rivate VLA N divides the Layer 2 b roadcast domain of a VLA N into subdomains and are particularly useful for service providers who need to assign a unique VLAN to each of their customers. Each subdomain is mad e up of sev eral pairs of private VLANs, with each private VL AN pair consisting of a primary and secondary VLAN. All of the VLAN pairs in a private VLAN domain are members of the same primary VLAN. Each subdomain is identified using the secondary VLAN ID. The diagram below illustrates the structure of a Private VLAN domain: Figure 3 - 10. Private VLAN domain The ports in a private VLAN can be one of the following three types: Port Type Description Promiscuous A promiscuous port is a port that is a member of a primary VLAN that can communicate with all interfaces, including ports that have been configured as community and isolated ports on secondary VLANs that are associated with the primary VLAN. Isolated An isolated port is used to describe a host port that is a member of an isolated secondary VLAN. An isolated port is completely isolated at Layer 2 from other ports within the same private VLAN domain, apart from promiscuous ports. All traffic destined to isolated ports is blocked, except for traffic originating from promiscuous ports. Any traffic originating from an isolated port is only forwarded to promiscuous ports. Community A community port is used to describe a host port that is a member of a community secondary VLAN. A community port can communicate with both ports that are members of the same community VLAN and promiscuous ports. Interfaces that are configured as community ports are isolated at Layer 2 from all other interfaces that are members of a different community and from isolated ports that are members of the same private VLAN domain. 71