D-Link DGS-3200-10 Product Manual - Page 177
MAC Local Settings, Web-based Access Control (WAC) - d link default ip
 |
UPC - 790069306310
View all D-Link DGS-3200-10 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 177 highlights
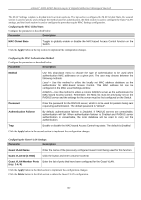
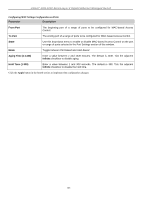
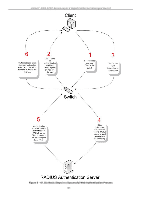
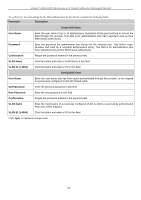
xStack® DGS-3200 Series Layer 2 Gigabit Ethernet Managed Switch MAC Local Settings Users can set a list of M AC addresses, along with their corresponding target VLAN, which will be authenticated for the Switch. Once a queried MAC a ddress is m atched in this wi ndow, it will be placed in the VLAN associated with it he re. The Switch administrator may enter up to 128 MAC addresses to be authenticated using the local method configured here. To view the following window, click Security > MAC-based Access Control (MAC)> MAC Local Settings: Figure 5 - 46. MAC Local Settings window To add a MAC address to t he local aut hentication list, en ter the MAC address and the target VLAN Nam e into their appropriate fields and click Add. To change a M AC address or a VL AN in the list, enter its parameters into the appropriate fields and click Edit. To d elete a MAC address en try, en ter its parameters in to th e appro priate field s and click Delete By MAC. To d elete a VLAN Name, enter its parameters into the appropriate fields and click Delete By VLAN. To search for a specific MAC Address, enter the MAC address in the first field and then click the Find By MAC button. To search for a specific VLAN Name, enter the VLAN name in the second field and then click the Find By VLAN button. Web-based Access Control (WAC) Web-based Authentication Login is a feature designed to authenticate a user when the user is trying t o access the Internet via the Switch. The a uthentication process use s t he HTT P p rotocol. T he Switch en ters th e au thenticating stage whe n us ers attem pt to browse Web pages (e.g., http://www.dlink.com) through a Web browser. When the Switch detects HTTP packets and this port is un-authenticated, the Switch will launch a pop-up user name and password window to query users. Users are not able to access the Internet until the authentication process is passed. The Switch can be the authentication server itself and do the authentication based on a local database, or be a RADIUS client and perform th e au thentication process via the RADIUS protocol with a rem ote RADIUS server. Th e clien t user in itiates th e authentication process of WAC by attempting to gain Web access. D-Link's implementation of WAC uses a virtual IP that is exclusively used by the WAC function and is not known by any other modules of the Switch. In fact, to avoid affecting a Switch's other features, WAC will only use a virtual IP address to communicate with hosts. Thus, all authentication requests must be sent to a virtual IP address but not to the IP address of the Switch's physical interface. Virtual IP works like this, when a host PC communicates with the WAC Switch through a virtual IP, the virtual IP is transformed into the physical IPIF (IP interface) address of the Switch to make the communication possible. The host PC and other servers' IP configurations do not depend on the virtual IP of WAC. The virtual IP does not respond to any ICMP packets or ARP requests, which means it is not allowed to configure a virtual IP on the same subnet as the Switch's IPIF (IP interface) or the same subnet as the host PCs' subnet. As all packets to a virtual IP from authenticated and authenticating hosts will be trapped to the Switch's CPU, if the virtual IP is the same as other servers or PCs, the hosts on the WAC-enabled ports cannot communicate with the server or PC which really own the IP address. If the hosts need to access the server or PC, the virtual IP cannot be the same as the one of the server or PC. If a host PC uses a proxy to access the Web, to make the authentication work properly the user of the PC should add the virtual IP to the exception of the proxy configuration. Whether or not a virtual IP is specified, users can access the WAC pages through the Switch's system IP. When a virtual IP is not specified, the authenticating Web request will be redirected to the Switch's system IP. The Switch's implementation of WAC features a user-defined port number that allows the configuration of the TCP port for either the HTTP or HTTPS protocols. This TCP port for HTTP or HTTPS is used to identify the HTTP or HTTPS packets that will be trapped to the CPU for authentication processing, or to access the login page. If not specified, the default port number for HTTP is 80 and the default port number for HTTPS is 443. If no protocol is specified, the default protocol is HTTP. The following diagram illustrates the basic six steps all parties go through in a successful Web Authentication process: 164