D-Link DGS-3200-10 Product Manual - Page 270
Appendix A - Mitigating ARP Spoofing Attacks, Using Packet Content ACL
 |
UPC - 790069306310
View all D-Link DGS-3200-10 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 270 highlights
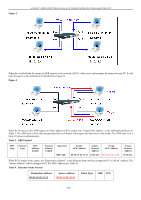
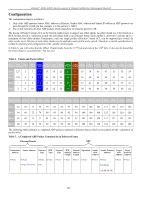
xStack® DGS-3200 Series Layer 2 Gigabit Ethernet Managed Switch Appendix A - Mitigating ARP Spoofing Attacks Using Packet Content ACL How Address Resolution Protocol works Address Resolution Protocol (ARP) is the standard method for finding a host's hardware address (MAC address) when only its IP address is known. Howe ver, this prot ocol is vulnerable because hac kers can spoof the IP and MAC info rmation in the ARP packets t o attack a L AN (known as ARP spoofing). This doc ument i s int ended t o i ntroduce t he ARP pr otocol, ARP sp oofing attacks, and the countermeasures brought by D-Link's switches to thwart ARP spoofing attacks. In the process of ARP, PC A will first issu e an ARP request to query PC B's MAC address. Th e network structure is sho wn in Figure 1. Figure 1 C Who is 10.10.10.2? A Sender 00-20-5C-01-33-33 10.10.10.3 D Port 3 Port 4 Port 1 Port 2 00-20-5C-01-11-11 10.10.10.1 B Target 00-20-5C-01-44-44 10.10.10.4 00-20-5C-01-22-22 10.10.10.2 In the meantime, PC A's M AC address will be written into the "Sender H/W Address" and its IP address will be written into the "Sender Protocol Address" in the ARP payload. As PC B's MAC address is unknown, the "Target H/W Address" will be "00-0000-00-00-00," while PC B's IP address will be written into the "Target Protocol Address," shown in Table1. Table 1. ARP Payload H/W Protocol Type Type H/W Address Length Protocol Address Length Operation ARP request Sender H/W Address 00-20-5C-01-11-11 Sender Protocol Address 10.10.10.1 Target H/W Address 00-00-00-00-00-00 Target Protocol Address 10.10.10.2 The ARP request will be encapsulated into an Ethernet frame and sent out. As can be seen in Table 2, the "Source Address" in the Ethernet frame will be PC A's MAC add ress. Since an ARP request is sent via broadcast, the "Destination address" is in a format of Ethernet broadcast (FF-FF-FF-FF-FF-FF). Table 2. Ethernet Frame Format Destination Address Source Address Ether-Type ARP FCS FF-FF-FF-FF-FF-FF 00-20-5C-01-11-11 When the switch receives the frame, it will check the "Source Address" in the Ethernet frame's header. If the address is not in its Forwarding Table, the switch will learn PC A's MAC and the associated port into its Forwarding Table. Forwarding Table Port 1 00-20-5C-01-11-11 In addition, when the switch receives the broadcasted ARP request, it will flood the frame to all ports except the source port, port 1 (see Figure 2). 257