D-Link DGS-3200-10 Product Manual - Page 183
Japanese Web-based Access Control (JWAC), JWAC Global Settings
 |
UPC - 790069306310
View all D-Link DGS-3200-10 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 183 highlights
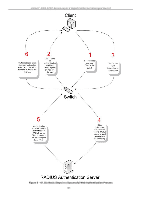
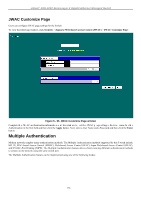
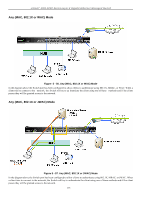
xStack® DGS-3200 Series Layer 2 Gigabit Ethernet Managed Switch Japanese Web-based Access Control (JWAC) The Japanese Web-based Access Contr ol (JWAC) f older c ontains fi ve windows: JWAC Gl obal Se ttings, JW AC Port Settings, JWAC User Settings, JWAC Customize Page Language, and JWAC Customize Page. JWAC Global Settings Users can enable and c onfigure Ja panese Web-based Access Control on th e Switch . Please note th at JWAC an d Web Authentication are m utually exclusi ve functions. That is, they cannot be ena bled at th e sam e time. To use the J WAC feat ure, computer users need to pass through two stages of authentication. The first stage is to do the authentication with the quarantine server an d th e secon d stag e is th e au thentication with the Switc h. Fo r the second stag e, t he au thentication is similar to Web Authentication, except that there is no port VLAN membership change by JWAC after a host passes authentication. The RADIUS server will share the server configuration defined by the 802.1X command set. To view the following window, click Security > Japanese Web-based Access Control (JWAC) > JWAC Global Settings: Figure 5 - 51. JWAC Global Settings window To set the Web authentication for the Switch, complete the following fields: Parameter Description JWAC State Use this drop-down menu to either enable or disable JWAC on the Switch. Authentication Failover Toggle between Enabled and Disabled. This is used to configure JWAC authentication failover. By default, the authentication failover is Disabled. If RADIUS servers are unreachable, the authentication will fail. When the authentication failover is Enabled, if RADIUS server authentication is unreachable, the local database will be used to do the authentication JWAC Configuration Virtual IP This parameter specifies the JWAC Virtual IP address that is used to accept authentication requests from an unauthenticated host. The Virtual IP address of JWAC is used to accept authentication requests from an unauthenticated host. Only requests sent to this IP will get a correct response. NOTE: This IP does not respond to ARP requests or ICMP packets. HTTP(s) Port (165535) This parameter specifies the TCP port that the JWAC Switch listens to and uses to finish the authenticating process. 170