D-Link DGS-3200-10 Product Manual - Page 172
Enable Method Lists, Enable Method Lists window, Parameter, Description
 |
UPC - 790069306310
View all D-Link DGS-3200-10 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 172 highlights
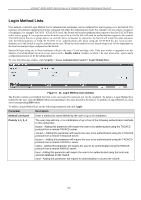
xStack® DGS-3200 Series Layer 2 Gigabit Ethernet Managed Switch Enable Method Lists Users can set up Method Lists to pro mote users with user lev el privileges to Ad ministrator (Ad min) level priv ileges using authentication methods on t he Swi tch. O nce a use r ac quires normal user l evel privileges on t he S witch, he or s he m ust be authenticated by a method on the Switch to gain administrator privileges on the Switch, which is defined by the Administrator. A maximum of e ight Enable Method Lists can be implemented on the Switch, one of which is a default Enable Method List. This default Enable Method List cannot be deleted but can be configured. The se quence of m ethods im plemented in this com mand will affect the au thentication result. F or exam ple, if a us er enters a sequence of m ethods lik e TACACS - XTACACS - Lo cal En able, the Switch will sen d an au thentication requ est to th e first TACACS host in th e serv er g roup. If no verification is found, th e Switch will sen d an au thentication requ est to th e second TACACS host in the server group and so on, until the list is ex hausted. At that point, the Switch will restart the same seq uence with the following protoc ol listed, XT ACACS. If no a uthentication ta kes place using t he XTACACS list, the L ocal E nable password set in the Switch is used to authenticate the user. Successful authentication using any of these methods will give the user an "Admin" privilege. NOTE: To set the Local Enable Password, see the next section, entitled Local Enable Password. To view the following window, click Security > Access Authentication Control > Enable Method Lists: Figure 5 - 42. Enable Method Lists window To delete an Enable Method List defined by the user, click the Delete button corresponding to the entry desired to be deleted. To modify an Enable Method List, click on its corresponding Edit button. To define an Enable Login Method List, set the following parameters and click Apply: Parameter Description Method List Name Priority 1, 2, 3, 4 Enter a method list name defined by the user of up to 15 characters. The user may add one, or a combination of up to four of the following authentication methods to this method list: local_enable - Adding this parameter will require the user to be authenticated using the local enable password database on the Switch. The local enable password must be set by the user in the next section entitled Local Enable Password. none - Adding this parameter will require no authentication to access the Switch. radius - Adding this parameter will require the user to be authenticated using the RADIUS protocol from a remote RADIUS server. tacacs - Adding this parameter will require the user to be authenticated using the TACACS protocol from a remote TACACS server. xtacacs - Adding this parameter will require the user to be authenticated using the XTACACS protocol from a remote XTACACS server. tacacs+ - Adding this parameter will require the user to be authenticated using the TACACS protocol from a remote TACACS server. 159