D-Link DGS-3200-10 Product Manual - Page 273
How ARP Spoofing Attacks a Network, Table 5
 |
UPC - 790069306310
View all D-Link DGS-3200-10 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 273 highlights
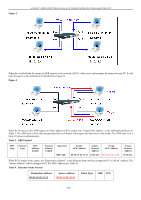
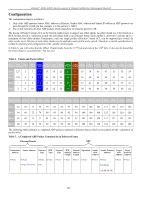
xStack® DGS-3200 Series Layer 2 Gigabit Ethernet Managed Switch How ARP Spoofing Attacks a Network ARP spoofing, also known as ARP poisoning, is a method to attack an Ethernet network which may allow an attacker to sniff data frames on a LAN, modify the traffic, or stop the traffic altogether (known as a Denial of Service - DoS attack). The principle of ARP spoofing is to send the fake or spoofed ARP messages to an Ethernet network. Generally, the aim is to associate the attacker's or random MAC address with the IP address of another node (such as the default gateway). Any traffic meant for that IP address would be mistakenly re-directed to the node specified by the attacker. IP s poofing at tack i s cau sed by G ratuitous ARP t hat occurs w hen a host sen ds a n AR P re quest t o re solve i ts own IP a ddress. Figure-4 shows a hacker within a LAN to initiate ARP spoofing attack. Figure 4 In the Gratu itous ARP p acket, the "Sender protocol address" and "Target p rotocol add ress" are filled with th e same sou rce IP address itself. The "Send er H/W Address" and "Target H/W add ress" are filled with th e same source MAC address itself. Th e destination MAC address is the Ethernet broadcast address (FF-FF-FF-FF-FF-FF). All nodes within the network will immediately update their own ARP table in accordance with the sender's MAC and IP address. The format of Gratuitous ARP is shown in the following table. Table 5 Ethernet Header Gratuitous ARP Destination Address Source Address Ethernet H/W Type Protocol H/W Protocol Operation Type Type Address Address Length Length Sender H/W Address Sender Protocol Address Target H/W Address Target Protocol Address (6-byte) (6-byte) (2-byte) (2-byte) (2-byte) (1-byte) (1-byte) (2-byte) (6-byte) (4-byte) (6-byte) (4-byte) FF-FF-FF-FF-FF-FF 00-20-5C-01-11-11 0806 ARP relay 00-20-5C-01-11-11 10.10.10.254 00-20-5C-01-11-11 10.10.10.254 A comm on DoS attack today ca n be done by ass ociating a nonexiste nt or an y sp ecified MA C a ddress to th e IP ad dress of th e network's default gateway. The malicious attacker only needs to broadcast one Gratuitous ARP to the network claiming it is the gateway so that the whole network operation will be turned down as all packets to the Internet will be directed to the wrong node. Likewise, the attacker can either choose to forward the traffic to th e actual default gateway (passive sniffing) or modify the data before forwarding it (m an-in-the-middle attack). The hacker cheats the victim PC that it is a router and cheats the router that it is the victim. As can be seen in Figure 5 all traffic will be then sniffed by the hacker but the users will not discover. 260