D-Link DGS-3200-10 Product Manual - Page 148
Guest VLAN, Limitations Using the Guest VLAN
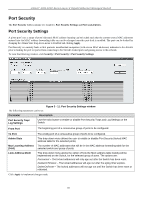
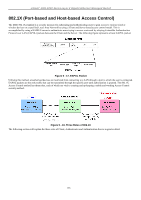
 |
UPC - 790069306310
View all D-Link DGS-3200-10 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 148 highlights
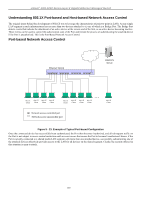
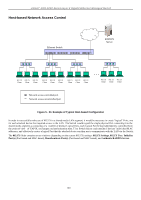
xStack® DGS-3200 Series Layer 2 Gigabit Ethernet Managed Switch Guest VLAN On 802 .1X secu rity-enabled n etworks, t here is a need fo r non 802.1X supported de vices to gain limited access to the net work, due t o l ack of t he p roper 80 2.1X s oftware or i ncompatible devices, s uch as c omputers r unning Windows 98 or ol der operating systems, or the ne ed for guests to gain access to the network without full authorization or l ocal authentication on the Switch. To s upplement these ci rcumstances, th is switch now implements 802.1X Gue st V LANs. These VLA Ns should ha ve limited access rights and feat ures separate from other VLANs on the network. To implement 802.1X Guest VLANs, the user must first create a VLAN on the network with limited rights and then enable it as an 802.1X guest VLAN. Then the administrator must configure the guest accounts accessing the Switch t o be placed i n a Guest VLAN when trying to access the Switch. Upon initial entry to the Switch, the client wishing services on the Switch will need to be authenticated by a remote RADIUS Server or local authentication on th e Switch to be p laced in a fully op erational VLAN. If authenticated and t he a uthenticator possesses the VL AN placement information, that client will be ac cepted into the fully operational targ et VLAN and no rmal switch fu nctions will b e open to the client. If the authenticator does not have target VLAN placement inform ation, the clie nt will be ret urned to its originating VLAN. Yet, if the clien t is denied au thentication by the authenticator, it will be placed in the Guest VLAN where it has limited rights and access. The adjacent figure should give the user a better understanding of the Guest VLAN process. Limitations Using the Guest VLAN Figure 5- 15. Guest VLAN Authentication Process 1. Ports supporting Guest VLANs cannot be GVRP enabled and vice versa. 2. A port cannot be a member of a Guest VLAN and a static VLAN simultaneously. 3. Once a client has been accepted into the target VLAN, it can no longer access the Guest VLAN. 4. If a port is a member of multiple VLANs, it cannot become a member of the Guest VLAN. To view the following window, click Security > 802.1X > Guest VLAN: Figure 5 - 16. Guest VLAN window Remember, to set an 8 02.1X guest VLAN, the user m ust first configure a normal VLAN, which can be enabled here for guest VLAN status. The following fields may be modified to enable the 802.1X guest VLAN: Parameter Description VLAN Name Port Enter the pre-configured VLAN name to create as an 802.1X guest VLAN. Set the ports to be enabled for the 802.1X guest VLAN. Click Apply to implement the guest VLAN settings entered. Only one VLAN may be assigned as the 802.1X guest VLAN. 135