Dell PowerConnect W Clearpass 100 Software 3.7 Deployment Guide - Page 106
Managing Certificates for External Authentication Servers, Client Private Key, Passphrase
 |
View all Dell PowerConnect W Clearpass 100 Software manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 106 highlights
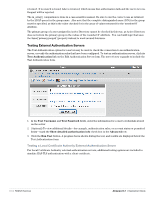
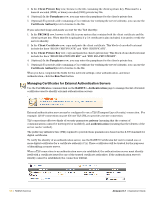
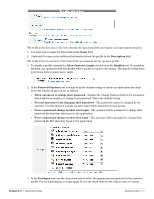
3. In the Client Private Key row, browse to the file containing the client's private key. This must be a base-64 encoded (PEM) or binary encoded (DER) private key file. 4. (Optional) In the Passphrase row, you may enter the passphrase for the client's private key. 5. (Optional) To provide a file containing a CA certificate for verifying the server's identity, you can use the Certificate Authority row to browse to the file. If you selected Copy and paste as text for the TLS identity: 1. In the PKCS#12 row, browse to the file in your system that contains both the client certificate and the client's private key. When this file is uploaded, if a CA certificate is also included, it is used to verify the server's identity. 2. In the Client Certificate row, copy and paste the client certificate. This block of encoded text must include the lines "BEGIN CERTIFICATE" and "END CERTIFICATE". 3. In the Client Private Key row, copy and paste the client's private key. This block of encoded text must include the lines "BEGIN RSA PRIVATE KEY" and "END RSA PRIVATE KEY". 4. (Optional) In the Passphrase row, you may enter the passphrase for the client's private key. 5. (Optional) To provide a file containing a CA certificate for verifying the server's identity, you can use the Certificate Authority row to browse to the file. When you have completed the fields for the network settings, outer authentication, and inner authentication, click the Run Test button. Managing Certificates for External Authentication Servers Use the Certificates command link on the RADIUS > Authentication page to manage the list of trusted certificates used to identify external authentication servers. External authentication servers may be configured to use a TLS (Transport Layer Security) connection. For example, LDAP connections on port 636 use TLS (SSL) to provide a secure connection. TLS connections offer two kinds of security guarantees: privacy (meaning that the content of communications cannot be intercepted or modified), and authentication (meaning that the identity of the server can be verified). The public key infrastructure (PKI) required to provide these guarantees is based on the X.509 standard for digital certificates. To verify the identity of an authentication server, use the RADIUS Certificates list view to install one or more digital certificates for a certificate authority (CA). These certificates will be trusted for the purposes of identifying a remote server. When a TLS connection to an authentication server is established, the authentication server must identify itself with a certificate issued by one of the trusted certificate authorities. If the authentication server's identity cannot be established, the connection will fail. 106 | RADIUS Services Amigopod 3.7 | Deployment Guide