D-Link DES-3528 Product Manual - Page 218
Authenticator State, Limitations Using the Guest VLAN
 |
UPC - 790069314346
View all D-Link DES-3528 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 218 highlights
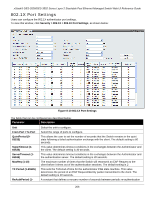
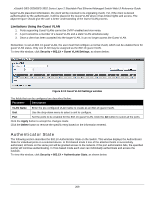
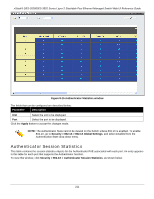
xStack® DES-3528/DES-3552 Series Layer 2 Stackable Fast Ethernet Managed Switch Web UI Reference Guide target VLAN placement information, the client will be returned to its originating VLAN. Yet, if the client is denied authentication by the authenticator, it will be placed in the Guest VLAN where it has limited rights and access. The adjacent figure should give the user a better understanding of the Guest VLAN process. Limitations Using the Guest VLAN 1. Ports supporting Guest VLANs cannot be GVRP enabled and vice versa. 2. A port cannot be a member of a Guest VLAN and a static VLAN simultaneously. 3. Once a client has been accepted into the target VLAN, it can no longer access the Guest VLAN. Remember, to set an 802.1X guest VLAN, the user must first configure a normal VLAN, which can be enabled here for guest VLAN status. Only one VLAN may be assigned as the 802.1X guest VLAN. To view this window, click Security > 802.1X > Guest VLAN Settings, as shown below: Figure 8-13 Guest VLAN Settings window The fields that can be configured are described below: Parameter Description VLAN Name Enter the pre-configured VLAN name to create as an 802.1X guest VLAN. Unit Use the drop-down menu to select a unit to configure. Port Set the ports to be enabled for the 802.1X guest VLAN. Click the All button to select all the ports. Click the Apply button to accept the changes made. Click the Delete button to remove the specific entry based on the information entered. Authenticator State The following section describes the 802.1X Authenticator State on the Switch. This window displays the Authenticator State for individual ports on a selected device. In Port-based mode if one of the attached hosts is successfully authorized, all hosts on the same port will be granted access to the network. If the port authorization fails, the specified port(s) will continue authenticating. In Host-based mode each user can individually authenticate and access the network. To view this window, click Security > 802.1X > Authenticator State, as shown below: 209