D-Link DES-3528 Product Manual - Page 253
Compound Authentication Settings, IMPB + WAC/JWAC Mode, MAC+ IMPB Mode
 |
UPC - 790069314346
View all D-Link DES-3528 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 253 highlights
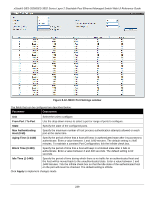
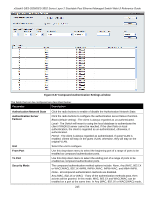
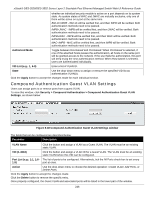
xStack® DES-3528/DES-3552 Series Layer 2 Stackable Fast Ethernet Managed Switch Web UI Reference Guide IMPB + WAC/JWAC Mode This mode adds an extra layer of security by checking the IP MAC-Binding Port Binding (IMPB) table before trying one of the supported authentication methods. The IMPB Table is used to create a 'white-list' that checks if the IP streams being sent by authorized hosts have been granted or not. In the above diagram, the Switch port has been configured to allow clients to authenticate using either WAC or JWAC. If the client is in the IMPB table and tries to connect to the network using either of these supported authentication methods and the client is listed in the white list for legal IP/MAC/port checking, access will be granted. If a client fails one of the authentication methods, access will be denied. MAC+ IMPB Mode This mode adds an extra layer of security by checking the IP MAC-Binding Port Binding (IMPB) table before trying one of the supported authentication methods. The IMPB Table is used to create a 'white-list' that checks if the IP streams being sent by authorized hosts have been granted or not. In the above diagram, the Switch port has been configured to allow clients to authenticate by using MAC. If the client is in the IMPB table and tries to connect to the network by using MAC and the client is listed in the white list for legal IP/MAC/port checking, access will be granted. If a client fails one of the authentication methods, access will be denied. Compound Authentication Settings Users can configure Authorization Network State Settings and compound authentication methods for a port or ports on the Switch. To view this window, click Security > Compound Authentication > Compound Authentication Settings, as shown below: 244