D-Link DES-3528 Product Manual - Page 281
Safeguard Engine Settings, IPv4 Address, Net Mask, Access Interface, Delete All
 |
UPC - 790069314346
View all D-Link DES-3528 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 281 highlights
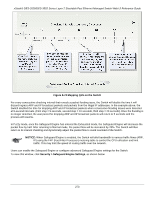
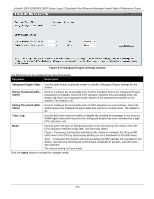
xStack® DES-3528/DES-3552 Series Layer 2 Stackable Fast Ethernet Managed Switch Web UI Reference Guide When the user clicks the Edit button, one will be able to edit the service allowed to the selected host. The fields that can be configured are described below: Parameter Description IPv4 Address Enter an IPv4 address to add to the trusted host list. IPv6 Address Enter an IPv6 address to add to the trusted host list. Net Mask Enter a Net Mask address to add to the trusted host list. Access Interface Tick the check boxes to select services that will be allowed to the trusted host. Click the Add button to add a new entry based on the information entered. Click the Delete All button to remove all the entries listed. Safeguard Engine Settings Periodically, malicious hosts on the network will attack the switch by utilizing packet flooding (ARP Storm) or other methods. These attacks may increase the switch load beyond its capability. To alleviate this problem, the Safeguard Engine function was added to the Switch's software. The Safeguard Engine can help the overall operability of the Switch by minimizing the workload of the Switch while the attack is ongoing, thus making it capable to forward essential packets over its network in a limited bandwidth. The Safeguard Engine has two operating modes that can be configured by the user, Strict and Fuzzy. In Strict mode, when the Switch either (a) receives too many packets to process or (b) exerts too much memory, it will enter the Exhausted mode. When in this mode, the Switch will drop all ARP and IP broadcast packets and packets from un-trusted IP addresses for a calculated time interval. Every five seconds, the Safeguard Engine will check to see if there are too many packets flooding the Switch. If the threshold has been crossed, the Switch will initially stop all ingress ARP and IP broadcast packets and packets from un-trusted IP addresses for five seconds. After another five-second checking interval arrives, the Switch will again check the ingress flow of packets. If the flooding has stopped, the Switch will again begin accepting all packets. Yet, if the checking shows that there continues to be too many packets flooding the Switch, it will stop accepting all ARP and IP broadcast packets and packets from un-trusted IP addresses for double the time of the previous stop period. This doubling of time for stopping these packets will continue until the maximum time has been reached, which is 320 seconds and every stop from this point until a return to normal ingress flow would be 320 seconds. For a better understanding, please examine the following example of the Safeguard Engine. 272