D-Link DES-3528 Product Manual - Page 255
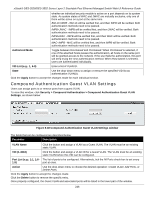
Compound Authentication Guest VLAN Settings
 |
UPC - 790069314346
View all D-Link DES-3528 manuals
Add to My Manuals
Save this manual to your list of manuals |
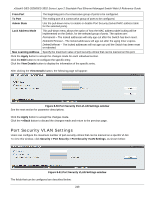
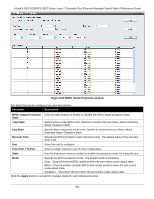
Page 255 highlights
xStack® DES-3528/DES-3552 Series Layer 2 Stackable Fast Ethernet Managed Switch Web UI Reference Guide whether an individual security module is active on a port depends on its system state. As system states of WAC and JWAC are mutually exclusive, only one of them will be active on a port at the same time. 802.1X+IMPB - 802.1X will be verified first, and then IMPB will be verified. Both authentication methods need to be passed. IMPB+JWAC - IMPB will be verified first, and then JWAC will be verified. Both authentication methods need to be passed. IMPB+WAC - IMPB will be verified first, and then WAC will be verified. Both authentication methods need to be passed. MAC+IMPB - MAC will be verified first, and then IMPB will be verified. Both authentication methods need to be passed. Authorized Mode Toggle between Host-based and Port-based. When Port-based is selected, if one of the attached hosts passes the authentication, all hosts on the same port will be granted access to the network. If the user fails the authorization, this port will keep trying the next authentication method. When Host-based is selected, users are authenticated individually. VID List (e.g.: 1, 6-9) Enter a list of VLAN ID. State Use the drop-down menu to assign or remove the specified VID list as authentication VLAN(s). Click the Apply button to accept the changes made for each individual section. Compound Authentication Guest VLAN Settings Users can assign ports to or remove ports from a guest VLAN. To view this window, click Security > Compound Authentication > Compound Authentication Guest VLAN Settings, as shown below: Figure 8-48 Compound Authentication Guest VLAN Settings window The fields that can be configured are described below: Parameter Description VLAN Name Click the button and assign a VLAN as a Guest VLAN. The VLAN must be an existing static VLAN. VID (1-4094) Click the button and assign a VLAN ID for a Guest VLAN. The VLAN must be an existing static VLAN before this VID can be configured. Port List (e.g.: 1:1, 1:6- The list of ports to be configured. Alternatively, tick the All Ports check box to set every 1:9) port at once. Action Use the drop-down menu to choose the desired operation: Create VLAN, Add Ports, or Delete Ports. Click the Apply button to accept the changes made. Click the Delete button to remove the specific entry. Once properly configured, the Guest VLAN and associated ports will be listed in the lower part of the window. 246